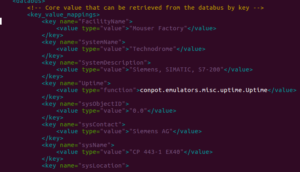
Time for an update on my constellation of honeypots. As you may recall from my last update, I currently have four Dionaea honeypots running in NYC, Frankfurt, Bangalore and Singapore (the GRAB series) and a single Conpot running in NYC (JUMPSEAT).
I had a bit of an issue this month that caused me to lose some data from the honeypots. The issue was the same on all the GRAB honeypots, but the circumstances were different and this is what’s interesting to me. I ran out of inodes on all four honeypots. On two of them (NYC and Frankfurt), this is definitely my fault as I never backed up and removed the bistreams stored on both of them, so after almost two months of operation I simply ran out of inodes there. However, on my other two, what was pretty crazy is that I ran out of inodes shortly after bringing them online due to the high volume of traffic on both honeypots. One honeypot ran out of inodes after seven days, and the other after three days due to the sheer volume of attacks. I didn’t think I’d have to check on them that frequently, but looks like we’re doing ok now. Maybe there was some sort of campaign in that part of the world… Here are the stats.
GRAB-NYC03:
Connections: 757,521
Unique IPs: 19,192
Files Downloaded: 12
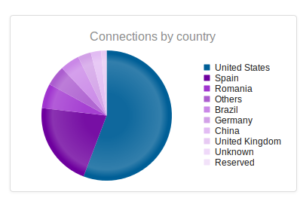
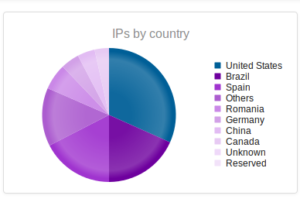
Similar results to last time I measured – though keep in mind that I did lose about 10 days of data from this one, so the full results probably would have been much higher. Romania increased its share to about 6% of the total attacks (up from about 0.71% last month).
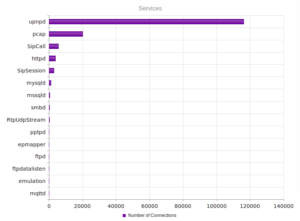
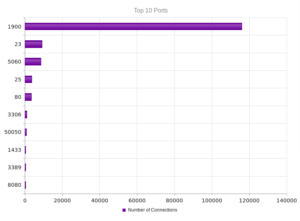
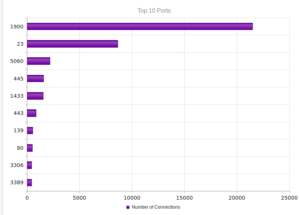
A more varied mix of services, while UPnP remains the most popular.
Again, not a shock that the most activity also came through port 1900, the UDP port for UPnP.
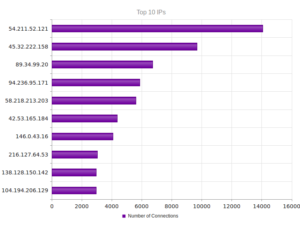
Actually a new set of top 10 IPs this time, with fewer attacks per IP address than last month (which had one address responsible for about 80,000 attacks). The top IP with 14,057 attacks leads back to AWS. The next one, 45.32.222.158, leads to Choopa, LLC, a managed hosting company in Matawan, NJ. According to their Google reviews, they are known for hosting malicious actors. Good to keep in mind in case I ever need a “permissive” host someday. Number 4 on the list, 94.236.95.171, is odd because it originates at Beggars Group, Ltd, a group of record labels. Numbers 5 and 6 originate in Beijing.
Here’s a map showing the attacker locations:
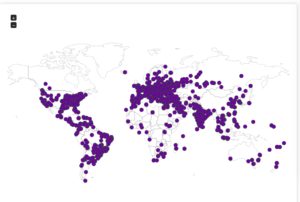
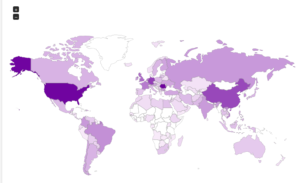
Next is the Frankfurt honeypot:
GRAB-FRA01:
Connections: 745,068
Unique IPs: 13,803
Files Downloaded: 13
Again, results more or less in line with last month, keeping in mind the loss of 10 days of data. More unique IPs this time, many fewer files downloaded.
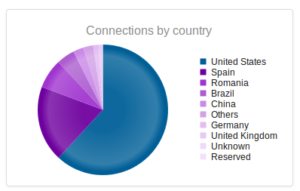
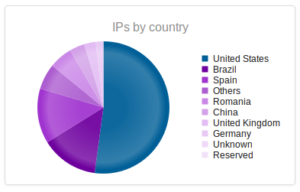
Similar to the results from the NYC honeypot.
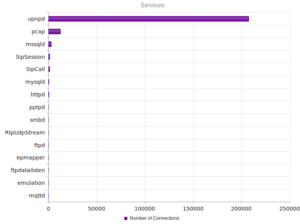
The huge number of UPnP connections looks more like the prior month’s results (compared with NYC’s results).
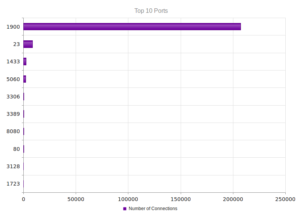
Therefore, no shock here when looking at ports.
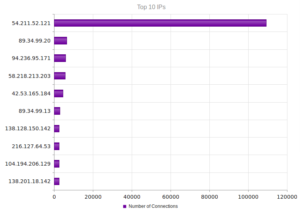
Like NYC, a new set of characters this time around. Nearly 110,000 attacks from 54.211.52.121, which leads back to AWS. In number 3, 94.236.95.171, we again see that Beggars Group, Ltd entity. Numbers 4 and 5 lead back to Beijing.
Here’s another map of the attackers, with an alternate view of the same data as well:
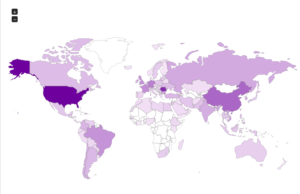
Now for the new honeypots!
GRAB-SIN01:
Connections: 154,834
Unique IPs: 17,750
Files Downloaded: 2,003
That’s not a mistake – I really did get just over 2,000 files collected in the Singapore honeypot. Almost all of them were Conficker variants. Out of all the unique binaries, I only found one Pepex variant and a Poebot variant, then 137 different Conficker binaries. I haven’t found Conficker in any of my other honeypots so far. Really unbelievable how many files I captured in such a small attack surface (compared with my other honeypots).
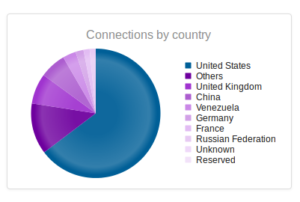
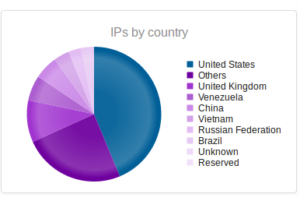
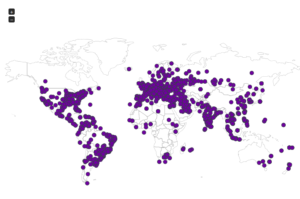
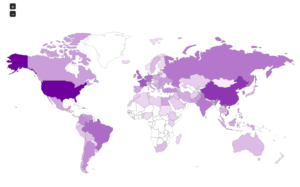
Interesting split – this makes me think that there is some sort of regional difference here, at least compared with my other honeypots. We see China higher up and also Vietnam, which so far I haven’t seen in the top 10 anywhere else.
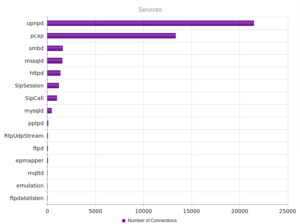
A bit more diversity in these services, closer to what NYC looked like vs. Frankfurt.
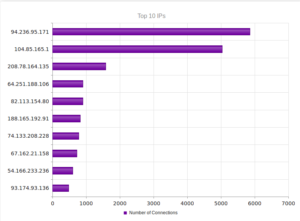
This time, Beggars Group is the top IP address messing around with my Singapore honeypot. Coming in at number 3 is 208.78.164.135, at Valve Corporation. Number 6, 188.165.192.91, leads to OVH in France. Number 9, 54.166.233.236, shows up as AWS. The final one there, 93.174.93.136, leads to Quasi Networks, based in Seychelles. Their barely functioning website advises that they are building sites in Amsterdam, Stockholm, Frankfurt, Moscow and London and that their website will be online soon. I guess they already have the hosting up and running… Another one to keep in mind in case I need a permissive host. Interesting that this hub didn’t see any Chinese addresses in the top 10.
Bangalore:
GRAB-BAN01:
Connections: 72,685
Unique IPs: 19,299
Files Downloaded: 1
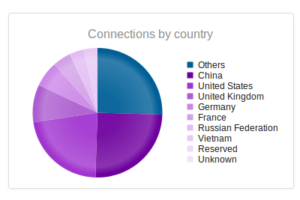
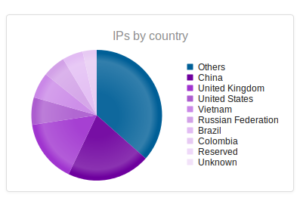
Dismal number of files collected from Bangalore. Interesting that this honeypot has the highest number of unique IPs of all the GRAB honeypots. Also interesting that this honeypot has the highest diversity of connections (the top is “Other” which encompasses individual countries that were too small to fit on the top 10 on their own, followed by China and the USA).
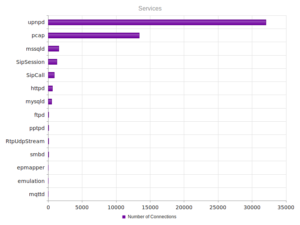
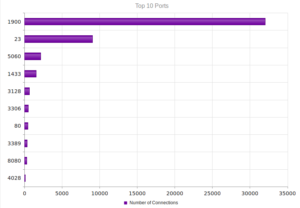
Nothing too out of the ordinary in terms of services and ports:
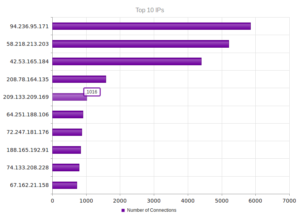
Beggars Group, Ltd, is number 1 again, at 94.236.95.171. Numbers 2 and 3 are in Beijing, number 4 is Valve Corporation again. We saw OVH again, in 8th place, at 188.165.192.91. Otherwise, nothing too new or interesting here.
Some maps:
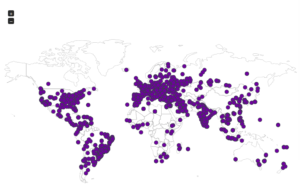
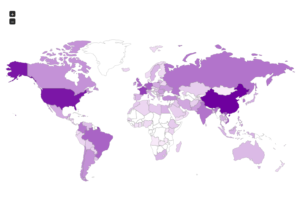
With JUMPSEAT, I’m running a Conpot honeypot, and I don’t have as many options as far as reporting as I do with the Dionaea honeypots. I took the raw logs and did some work with them in LibreOffice. Here are some numbers regarding the total numbers of connections that I had:
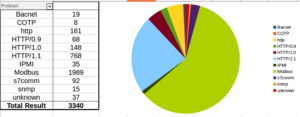
Modbus was the most popular protocol, followed by all variants of HTTP. There were a few other things scattered around in there. Looking at attacks by IP address, things get more interesting:
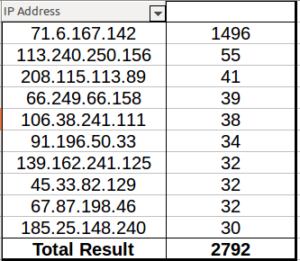
71.6.167.142 leads to a hosting company called CariNet out in San Diego, CA. This person scanned just about every port on JUMPSEAT. The other addresses were definitely more typical of the activity I got on this honeypot, as you can see from the numbers. 113.240.250.156 and 106.38.241.111 lead to Beijing. 91.196.50.33 and 185.25.148.240 lead back to a hosting company in Poland. 67.87.198.46 actually leads to Optimum Online in NY – is someone scanning these from home?
When I ran 71.6.167.142 through robtex.com, it actually appears that this is shodan.io. The way it scanned the honeypot makes sense now.
That’s it for this month.