I decided to check out an unusual file I received in my Hotmail account. This one was much older (received in November of 2014) but I thought it was interesting because it was a 9 mb Rich Text file. The sender was [email protected]. Some excerpts from the letter can be found below in the raw notes. I think a nice touch is that the letter is signed “Mr. Andrew Moor” but the signature appears to be Abraham Lincoln’s.
I went through the RTF specification looking for control words that could offer information about the author or lead to code execution and the like. Checking various tags didn’t reveal much, however I did see some info such as:
Author: user [oh, him]
Operator: PC13
Company: egyptian hak
Generator: Microsoft Word 11.0.5604
The reference to Egyptian Hak is a whole other topic that I might address at some point, but for now let’s leave it at this: There seems to be a cracked version of Windows XP SP3 (that comes packaged with several cracked utilities) circulating through the Arabic-speaking world (and concentrated in Egypt) and it was created by someone calling themselves Egyptian Hak. At some point I’d like to sit down and really dig into this but that’s all I want to do for now. My working assumption is that whoever created this document was running a copy of this XP “variant”, if you could call it that.
The version and build of this version of Word is interesting. The version indicates that this document was created with Word 2003. I would expect to see two numbers, one indicating the build number for the program and the second for build of the core Office shared library (MSO). This build number doesn’t seem to adhere to this format, but according to David Vielmetter’s website, this appears to be an original MS Office Word 2003 build (i.e., not a Service Pack build).
There is a reference to a website in this file:
This is interesting to me because this link goes to what appears to be a legitimate website and organization (a museum in British Columbia). I wonder if 1) this is a legitimate image that happens to have been hosted there for legitimate reasons that has been appropriated by the document author or 2) if this image itself is malicious and/or was put there due to some sort of unauthorized access on the part of the document author.
Running this through various sandboxes revealed nothing too special. I’m a bit frustrated because it seems like I have this document file that doesn’t seem to be much else other than a written scam (no links, no executables, no shellcode signatures detected, etc.). Opening the file didn’t indicate anything happening – no files written/dropped (aside from the usual), no network traffic, no registry changes. I can’t believe that people would bother to send out documents that are nothing more than form letters – I could be looking for something that isn’t there, so I should be careful not to find things that aren’t there, but I also feel like I need to dig deeper into this sample.
My next step was to look through the document for anything that might indicate shellcode. Where the images are displayed in the Rich Text Format, you see lots of raw data:
I searched the text of the file for any sections that might look like code to convert to a binary file. As you can see, there were two strings with three instances of NOP which are going to be where I’ll focus. The first hit at offset 0x8B20E3 also had three instances of opcode 0x4F, which would be DEC EDI in x86 assembly, following the NOPs (these two groups being separated by 00). The second group of NOPs at offset 0x8B1C8A didn’t have any opcodes in the 0x40 to 0x4F range following it, but I’ll look at that offset anyway.
I searched for occurrences of at least three of the following opcodes, and I got the following results:
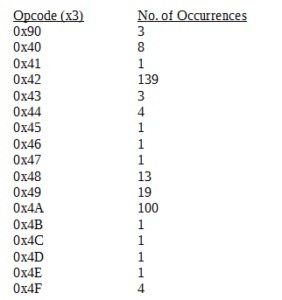
My list of “interesting” offsets, such as the already mentioned triple NOPs and also other areas where I saw many possible opcodes together (e.g., a string like 4242424A4A4A424242 or up to five occurrences of the same potential opcode) is as follows:
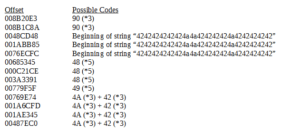
At this point, I feel that these are probably the most promising areas to look at in terms of possible shellcode. To save the trouble of converting these sections into binary files, I decided to use the online disassembler at disassembler.io again.
Going through the disassembly of all these areas was disappointing, as it all resulted in garbage. I even put the entire file through just to see if anything stood out, and nothing resulted. The .JPG that the file links to didn’t have any triple occurrences (or more) or any of these opcodes either.
I’m pretty much at a dead end with this one. I also went back through procmon in detail and didn’t see anything interesting going on in the system. If nothing else this was a good exercise on the Rich Text Format. I’m also going to reach out to the website’s admin and see if they know about this file and how it’s being used.
References:
davidvielmetter.com/tips/microsoft-office-executable-version-numbers/
blogs.msdn.microsoft.com/jensenh/2005/11/11/decoding-office-build-numbers/
Findings and observations:
RTF file containing written instructions for some sort of financial scam, clumsily executed. Possible Arabic speaker as author. No dynamic behavior observed myself or via sandbox.
Recommendations:
Usual guidelines against opening strange attachments still stand. Admin of the site linking the image might want to review security, specifically around how that file appeared on their site.
Conclusion:
Scam message, no apparent malicious activity. Possible that any exploits in this sample might just not be effective running on the current test system.
Report:
MalRTF_001
Hashes
MD5:e2e2d91211ed870d44c6df85f58976fe
SHA1:3d2ec090b308e27e4490a3082901784110e06324
SHA256:66096c1c1692b8f1a4e8e9b678351601ded0a189241e7cbfeffc01c5bd379b93
ssdeep:24576:nOowJRsxdhW5DubB5UOG7Pz+UfOowJRsxdhW9DubB5UOG7Pz+UqOowJRsxdhWyDz:I