For the TL;DR on setting up Dionaea, see below
Lately I’ve been pretty disappointed in the kinds of attachments I’ve been receiving in my various emailboxes. Adwind (both iterations) was pretty interesting to see, but I’m noticing that a lot of what I receive is just a more formatted, fancier 419 scam. I’m basically just seeing various versions of “I’m a Nigerian oil minister, please send me your bank details” in a document attachment. I’ve actually even gotten one sender to resend their attachment as a PowerPoint file.
A couple of things occur to me, one is that these might be files that take advantage of vulnerabilities in older versions of the software that I am running, so when I open them on my current test environments I’m not really seeing anything happen. Going forward I’m going to run much older versions of my applications to see if anything different happens. For instance, I just put Acrobat Reader 5.0 on one of my testing VMs and used that to open a recent attachment during examination (though nothing happened with this ancient version of Acrobat, either). Another explanation is that these might just be exactly what they appear to be — prettier versions of the same crap that fills my inbox on a daily basis, but not much more than that.
I think it’s OK to continue checking my email attachments for stuff to analyze, but I also recognize that I need better samples, ideally Windows executables which I’m more knowledgeable about than documents. I decided to try setting up a honeypot to see if I could get anything interesting. I ran into various roadblocks along the way before I got something up and running, but hopefully detailing what happened might help others avoid some of these issues.
The first thing I noticed is the somewhat fragmented state of the various open-source honeypots out there. Dionaea was the most recommended one from various sources, but the original site (http://dionaea.carnivore.it/) is out of service and most material I managed to find about the software was from several years ago. I tried another honeypot, Amun, but that seemed sort of defunct at this point also. The last update (from 2012) stated that it was still being maintained, but the documentation section had most of the links struck out so it was a bit hard to figure out exactly what to do with it.
I decided to use my testing machine as the host for the honeypot since it’s already running Ubuntu. I got Amun set up on it and got it running, but strangely there seemed to be very little activity (something on the order of 3-4 pieces of traffic over a 2-3 day period). This seemed VERY strange to me — I was thinking that there would likely be hundreds of scans per day at least. I tried various things to get things working better:
– Disabled firewall on the host
– I thought that maybe there was some issue with NAT or something else, so I added the host machine to the router’s DMZ
– Temporarily disabling all security features on the router and observing if there were any changes
– I tried connecting the host directly to the cable modem here, not going through the router at all
Finally after about five days, I ended up with six scans. Something just didn’t seem right.
I decided that I would have to give Dionaea a try. Installing using repositories didn’t work, so I had to find out everything I’d need to install manually and then install from source. I’d also need to find the source since the main site wasn’t around anymore.
This site had the best set of Dionaea docs I could find. You can also find some info about using Dionaea in Malware Analyst’s Cookbook in the second chapter (specifically, recipes 2-4 through 2-9). I installed Dionaea from PhiBo’s github repository, however I also mirrored it to my newly created one since I feel like the world could always use more copies of this lying around.
Here are the steps I followed, largely following the instructions from the readthedocs.io link above. For the benefit of anyone who doesn’t do this often (or maybe is doing this for the first time), I’m putting explicit directions on what commands to enter:
- Update packages:
sudo apt-get update sudo apt-get dist-upgrade
- If you don’t already have it installed, install git:
sudo apt-get install git
- Install all Dionaea dependencies (note the one in bold — if you try to install the original libnl-dev mentioned in the docs you’ll get an error about it not existing, but you can use libnl-3-dev instead):
sudo apt-get install \ autoconf \ automake \ build-essential \ check \ cython3 \ libcurl4-openssl-dev \ libemu-dev \ libev-dev \ libglib2.0-dev \ libloudmouth1-dev \ libnetfilter-queue-dev \ libnl-3-dev \ libpcap-dev \ libssl-dev \ libtool \ libudns-dev \ python3 \ python3-dev \ python3-yaml \
- Put the repository in /opt/dionaea (use either of the repositories above, as an example I’ll use the one I created):
sudo git clone git://github.com/BYEMAN/dionaea.git /opt/dionaea
- Run the following commands:
cd /opt/dionaea sudo autoreconf -vi sudo ./configure \ --disable-werror \ --prefix=/opt/dionaea \ --with-python=/usr/bin/python3 \ --with-cython-dir=/usr/bin \ --with-ev-include=/usr/include \ --with-ev-lib=/usr/lib \ --with-emu-lib=/usr/lib/libemu \ --with-emu-include=/usr/include \ --with-nl-include=/usr/include \ --with-nl-lib=/usr/lib sudo make sudo make install
- To start an instance of Dionaea, you can just run it as a super user but I typically run it as a daemon and put the PID in a file, as suggested in the Malware Analyst’s Cookbook
sudo /opt/dionaea/bin/dionaea -p /opt/dionaea/var/dionaea.pid -D
That should be all you need to do in order to get the software itself running. How it works for you once up and running is another topic.
Shortly after getting the honeypot running, I noticed LOTS of logging activity and within about 5 hours I observed 2700 scans had come in. Obviously much different than with Amun. Not sure why this happened, but I also didn’t look into it since I was just happy to have a honeypot up and running.
After a couple of days, I had collected lots of traffic and recorded many sessions but didn’t manage to collect any binaries, which is really what I’m after here. I did some reading online and I saw some suggestions that quite often any binaries come in over the ports for SMB (445) and MSMQ (1801 and others). Googling revealed that my ISP blocks these ports for residential customers (though not for business users), and checking with canyouseeme.org confirmed that my machine was unreachable through these ports. I needed to get something, somewhere that would allow me to run the honeypot without these restrictions.
Someone I know recommended getting something on Digital Ocean and setting up a honeypot there. I signed up with them and so far I have to tell you that I’m pretty thrilled with them. I got the cheapest “droplet” which comes to $5 a month, and set it up with Ubuntu 16.04 and the honeypot. You can confirm what ports are open on their systems with ping.eu, but I also emailed their support before I signed up and got the following response:
We do have a few restrictions, on UDP port 80 traffic, and SMTP over IPv6, both to prevent abuse and which cannot be lifted. Otherwise, we don’t any network restrictions, so as long as your software is compatible with the Linux or FreeBSD distributions that we offer, it should run just fine.
Another thing that I thought was nice about them is that you can locate your droplet in datacenters in various parts of the world. I picked one in NYC, but I’m thinking about getting some set up in other regions to see if I get different traffic there. If you want to sign up, use this link and you’ll get $10 in credit from Digital Ocean assuming you’re new to them.
I spent an evening getting my droplet set up and installing Dionaea, and then let it run overnight. At 0753 the next morning:
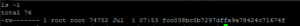
And look how it begins:
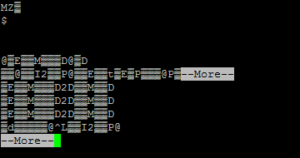
Nice.
Oh yeah, referring to the title — one of the first scans I received was from something identifying itself as “FRIENDLY-SCANNER”. Seems legit.