After a long break, I’ve decided to start posting material again. Last time I posted, it was to announce that I had just started doing malware analysis professionally. I’m still doing that, but now that I’ve gotten up to speed on my new role I wanted to start posting my own work again. I’m going to focus on things that I find interesting and also keep my work topics completely separate from my personal research. I’m also not going to focus on a strict timeline, because work demands often wreak havoc on any scheduling ideas I might have (the recent WanaCrypt0r incident is one such example). I’ll get to this stuff when I can, and post when I feel like it’s ready to go.
I’ve been interested in mobile malware for a while now, but we don’t cover that at work. I decided to take a look at what mobile malware is available on a certain underground forum and found several examples. On a separate but related topic, now that I’ve been doing this full time as my day job, I’ve learned that many malware developers try to hide behind claims that what they’re doing is either 1) creating “educational” malware to learn to code or 2) that they are peddling legitimate “system management” tools. Some good examples of these include Orcus RAT or NexusLogger (“protect your kids! Monitor your employees!”). Droidjack appears to be one of these Remote Admin “Tools” for Android devices. According to the DroidJack website (http://www.droidjack[.]net):
There is nothing that you can do with a PC that you can’t do using an Android phone. Since the power in the hand has grown so much, a control over that power is also needed. DroidJack is what you need for that. DroidJack gives you the power to establish control over your beloveds’ Android devices with an easy to use GUI and all the features you need to monitor them. [Emphasis mine]
Yes, because what we all need is to “control our beloveds…”. Total BS, and once you start to examine the software in more detail, you get to see the real picture painted by the developer.
On an underground forum, some kind individual uploaded a cracked DroidJack 4.4 builder with the following characteristics:
MD5 502b45d4d238e02f793a5b8669fa77fb
SHA1 6defd64dfde0bfdfec8b8d92371aa5d5dd5e4e95
SHA256 6dfef45751e209486aa714b8cf80fbd5b74b2f6f7c522bbb3a83c002ca3e5d6b
ssdeep:
393216:jf9tMySrGbauBeysCQTAjrW5yXkgKuRnKuU3R/T5GLaX:DQySSepbCQTarW54MuRCpEe
File size 17.9 MB ( 18811664 bytes )
Taking a look inside, there’s a readme file, let’s see what’s interesting in there:
Author:
——–
L.R Sanjeevi (c) 2015.
Good to know.
Setup Instructions:
——————–
1) Register a dynamic dns from no-ip or dnsdynamic.com
2) Choose a port (Example: 1337), forward the chosen port (1337) and 1334
(default) so u need to port forward 2 ports!
3) Generate the APK with the chosen port (1337) and ur dynamic dns and other details!
4) Do not scan it on virustotal or such sites so that it remains FUD longer.
Huh, well, that’s interesting right? There’s nothing necessarily wrong with places like VPS hosts, except that it’s common to see them hosting some shady stuff. But DroidJack is a legit tool, why do we need to go to these lengths? Also, don’t upload it to VT so that it stays FUD longer? For those unfamiliar with this term, FUD means Fully UnDetectable and is a common claim from skids uploading their tools to underground forums (and usually their garbage malware isn’t FUD anyway). Gee, sure seems pretty paranoid for a LEGITIMATE system management tool…
Ah, they have a helpful FAQ further down, here are some interesting questions and answers:
5) I have used the stealth mode but app icon is visible!
Ans) The app needs to be opened once at least then it will automatically hide the icon. In some devices after a reboot the icon will disappear.
6) I am getting an error when I try to bind with an app or game!
Ans) Try binding with a different app or game. Some apps or games will have checks when modifying so it will not allow modifications.
8) Can I use a different port instead of port 1334 (default port)?
Ans) No. Port 1334 must be opened only for DroidJack.
12) I am not able to upload files to the device!
Ans) Check if you have write access on that folder. You can see that by selecting the folder.
13) I am not able to delete SMS messages!
Ans) In Android 4.4 and above this feature will not work due to API restrictions.
So, there’s a stealth mode so the victim user can’t see that the RAT is installed… there’s a bind feature to bind the malware totally legit tool to an actual legitimate application… you can upload files to the device running DroidJack and apparently access SMS messages. Totally sounds like things you’d need to do for legitimate system management purposes.
The last line is sort of funny:
Feel free to contact me for support and suggest your ideas.
Uh, how about, stop writing malware?
OK, so looking in this thing, there are several files and folders in the builder after extraction. Looking in the Apktool folder, I see something called SandroRat.apk – Googling Sandro RAT results in a bunch of results regarding the targeting of banks using Sandro RAT in phishing. Such a legit tool! Maybe the developer of DroidJack stole this person’s work, or maybe it’s this dev’s work that’s being reused.
One thing that is nice about looking at something like Java (or .Net) is that because of the nature of the language, if you have the application, you typically have the source code (unless it’s been obfuscated, and even then you usually will get it). Scanning through the SandroRat.apk file, it looks like there’s code to support the following functionality:
- SMS activity logging and tracking
- Incoming / Outgoing / Draft SMS messages
- The malware grabs the following fields:
- FROMTXT
- CNAME
- FROMPHNO
- MDATE
- MYTXT
- TOPHNO
- Goes after Whatsapp data (via the msgstore.db file)
- Gathers contact info, browser and bookmark history, and call records
- Gets GPS / location information
- Turn screen on/off
- Gather device information (system inventory function):
- Brand
- Serial number
- Model
- OS version / release
- WiFi connection info (specifically the MAC address)
- Device IP address
- Device ID
- Phone network operator name
- List of installed apps
- Current running task list
- Recording of audio (sample rate 11025, encoding bitrate 128)
- Ability to turn on WiFi or mobile data in order to achieve connectivity with the RAT controller
- Take photos and record videos using the onboard cameras
- Update feature
- Phone state information (Offhook, Idle, etc.)
- Call recording
- Files will appear in the format “rec_*.amr” and will also log the date/time group of the call, state, and phone number
This file had numerous references to both Sandro RAT as well as DroidJack within it. Sort of makes me think that DroidJack is just the next iteration of Sandro RAT. Adding to this, looking inside the Droidjack.jar file (which is the main builder Java executable), one of the main blocks of code in there refers to Sandro RAT.
OK, let’s run this thing.
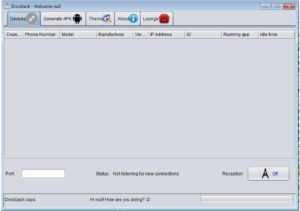
How friendly it is. The main panel is where you can view a summary of all of your victims, displaying their country, phone number, phone model and manufacturer, OS version, IP address, phone ID, the current running app and idle time. You’d think that if you were just using this for something “legitimate” like spying on your spouse or your kids that you would already know what country they’re in and their phone number… but anyway…
In the about tab, you can see that the developer isn’t shy about this:

Going to the Generate APK tab, we see this:
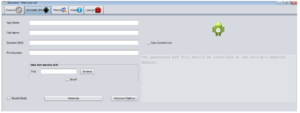
What’s that on the right? “The generated APK file should be installed on the victim’s Android device!” Wait, what? VICTIM? WHAT EVER DO YOU MEAN SIR, THIS IS A LEGITIMATE ADMIN TOOL… I’ll try to stop going off about this but can’t guarantee it. Anyway, here we can see the various characteristics we can set for the generated RAT client that would be used to infect a target device. These are App Name, File Name, Dynamic DNS provider, Port, Bind (so as to package your RAT with something actually legitimate), and the option to engage “Stealth Mode”.
The advanced options button brings up a new window with the following appearance:
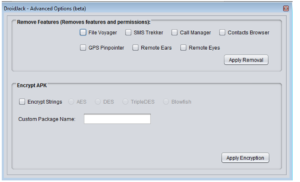
So it appears that you can disable certain functionality that we saw in the quick review of the Sandro RAT code, specifically access to and/or harvesting of files, SMS messages, call data, contacts, location data and the ability to remotely record audio and/or still or video images. It also looks like there’s an obfuscator built into this to obscure strings using AES, DES, TripleDES or Blowfish. I’m going to skip all this for now, but will come back to this later.
OK, I generated a sample of the client using the following parameters:
App name: totally-legit
File name: totally-legit
Dynamic DNS: 127.0.0.1
Port: 31337 (because I’m SUPAR 1337)
I guess I should also note that at this point I haven’t seen anything drop or observed any “strange” network activity, so it appears that this builder was leaked “clean”. Great, so now we have our totally-legit.apk file. Let’s take a look inside…and it’s basically exactly the same code as the Sandro RAT apk. All that discussion about Sandro RAT from before, just s/Sandro RAT/DroidJack/ and we’re pretty much done. However, let’s try applying some of the obfuscation to the clients and see what happens.
What I noticed is that while the clients do come out differently, I’m just not seeing how they are obfuscated when applying the various crypto methods to the clients. Opening each of these files in my tool just shows me all the strings in plaintext. The only thing that’s different is that when I built a “stealth” client, there were a couple new classes added (“oa” and “qa”) which appear to use a combination of Base64 and Blowfish to help obscure things. I must not be getting something, though, because when I try to apply crypto to obfuscate strings, I expect to not be able to see any strings anymore.
I hope all this was interesting. I don’t currently have an Android test environment up and running, so this was done all statically. I went ahead and uploaded the files that came out of all this, maybe you’ll find these and play around with them yourself. For my first time ever looking at something for a mobile device, I think this isn’t an awful first attempt at looking at a mobile RAT.
Some mitigation recommendations:
- Don’t download shady apps that might have something like DroidJack bound with it.
- Given that the RAT has to use port 1334 (and seems to like 1337), one could be aware of strange traffic on these ports.
- Given the functionality, one could try to observe the following indicators:
- If you observe strange files being saved on your device, such as the aforementioned “rec_*.amr” files or other indicators, that could possibly indicate this (or perhaps another) RAT is present on the device
- Also, unusual amounts of mobile data being used could indicate an infection, as this malware appears to be able to activate mobile data for connectivity purposes
- Finally, if the screen randomly or unintentionally turns itself on or off, this could also indicate something malicious present on the device
Here are the rest of the file hashes from DroidJack:
Sandro RAT .apk
MD5 9202458b25d8c56b85b5801c254c43e9
SHA1 97b1a631fd88b13327b00269f859f0e311b5ac93
SHA256
03ac348fc2978168bf86a1ba63a32f411e5642fbd11c95f59ff4d4c7e7b049c6
ssdeep6144:yuObopWPaR7mM++Iu8hK+CqoDTvJpsbV1dFqQOG8/8V4Sy8:yuObyjOu1+ToDTRpE1utDf8
File size 252.5 KB ( 258537 bytes )
https://www.hybrid-analysis.com/sample/03ac348fc2978168bf86a1ba63a32f411e5642fbd11c95f59ff4d4c7e7b049c6?environmentId=200
DroidJack Builder Main Executable
MD5 2f1d90b58522ebec2846c8dd27943b9c
SHA1 bc821c3ee2a4b86a08b4ec701cdb8fe79300b80c
SHA256
0842b4ac4b0c2198ea305f56fc5d649598a903dccfcbdd22ec22f2b0f68cb7be
ssdeep24576:lO0l4+lqJxEHBu6oF3NKfaHpvZwE+08jnt/o3Tim6xD8m:lBG++6ObJvOp0YSji/5
File size 1.6 MB ( 1675231 bytes )
https://www.hybrid-analysis.com/sample/0842b4ac4b0c2198ea305f56fc5d649598a903dccfcbdd22ec22f2b0f68cb7be?environmentId=100
Basic DroidJack Client
MD5 132f2b9f6775d51f2c776358f1176989
SHA1 2ecadde1b70c245d6725565ff1684468b3e2da31
SHA256 a664d235973da209501ef982754389b1515a96d7bee9dec6692dbe2d9b6a12ca
ssdeep6144:Eybt4/YCgynNsY3ShU7cM63ezK+Kylye4Rb/Il09UVGGOv:tWwXLYiM63eO+Ky0Rb/+6UVZOv
File size 254.4 KB ( 260475 bytes )
https://www.hybrid-analysis.com/sample/a664d235973da209501ef982754389b1515a96d7bee9dec6692dbe2d9b6a12ca?environmentId=200
Basic DroidJack Client (3DES)
MD5 e2391b89afbade0d1a95f653c9c89159
SHA1 e66f7b7ddb10f8e8311bd3b10bcbe0a79976a04e
SHA256 e1d10b2be5e94d4e16ed440a6a2bedc813e072dbed96eebb578345947128c7dassdeep6144:4yce4/wfBjdznG0Gy1YIAcplQ1C2mtYKhEMsDbwH7aqF8V1hV:5C4f1dhGyeI3plQRlDcH7ao8PhV
File size 264.8 KB ( 271171 bytes )
https://www.hybrid-analysis.com/sample/e1d10b2be5e94d4e16ed440a6a2bedc813e072dbed96eebb578345947128c7da?environmentId=200
Basic DroidJack Client (AES)
MD5 037065bbd4aa6deefff7cb0dbf015eb6
SHA1 2ed326cff4941759ea8d7011a705905801d8e9fb
SHA256 4553f97bff44cdafebab6b403ba7d1607a4720a85b9e63eac850b56049b4296d
ssdeep6144:5ny2w4lYCgynNsY3ShU7cM63ezK+Kylye4Rb/Il09UVGGOO:4qWXLYiM63eO+Ky0Rb/+6UVZOO
File size 254.4 KB ( 260479 bytes )
https://www.hybrid-analysis.com/sample/4553f97bff44cdafebab6b403ba7d1607a4720a85b9e63eac850b56049b4296d?environmentId=200
Basic DroidJack Client (Blowfish)
MD5 9c65c53a31b31c769efa7d7d01ae846b
SHA1 19b3a0f8e787ebb2c9b95f9ebd88d0a5181d2f92
SHA256
82c113ce99b9596db142e36de4ef54410213bd6df1f5f58df72d5392e0743a25
ssdeep6144:nyeo42MLxMh+BTENZZyQxERHyJVO43CtCV0MQ2mPxuGQeZW:yO2+xRBANnJxERSJV5CYV9sPxuuZW
File size 264.9 KB ( 271260 bytes )
https://www.hybrid-analysis.com/sample/82c113ce99b9596db142e36de4ef54410213bd6df1f5f58df72d5392e0743a25?environmentId=200
Basic DroidJack Client (DES)
MD5 b5c6dcc9e98463dbb06707d173bfa0ee
SHA1 b80b73fe66a2f846364d121d7591b32239f09abc
SHA256
80a785327ebbce92f43f2668581f5f55ca616b865d956adf89d92e56d86d680c
ssdeep6144:nyBF4j5NqMwyJPFcsPNsCqDz6002+RaIrKOKTH9UiF:y4j5NqXy5CsFODG00vRVXKjye
File size 264.7 KB ( 271088 bytes )
https://www.hybrid-analysis.com/sample/80a785327ebbce92f43f2668581f5f55ca616b865d956adf89d92e56d86d680c?environmentId=200
Basic DroidJack Client (Stealth)
MD5 0ed3e8f1dff311602aae835b5aa931a3
SHA1 b52a9fb2f93c2a2e724bdc48894fd3d290668b5f
SHA256 19a07f586fc7b52123ff20751a8601f03aa48fee248d33e231f79a27eeca27bb
ssdeep6144:kyWh4diqGpPtW5363otvNDwPnZRQZzegBk3WdmM73H:NXdiqaPtW5fvN0PZRGzeuE0mM3H
File size 264.8 KB ( 271122 bytes )
https://www.hybrid-analysis.com/sample/19a07f586fc7b52123ff20751a8601f03aa48fee248d33e231f79a27eeca27bb?environmentId=200