I was recently looking through a certain community of 1337 hax0rs and found someone trying to promote some malware that they allegedly cracked [Note: as I researched this, I later learned that the actual developer never charged for this RAT, so just the fact that the person who linked to this sample claimed to have cracked it shows that something’s up]. One of these is called Darktrack RAT, and the other is Reaper ransomware.
Jump to:
Static and Dynamic Analysis
Disassembly
Debugging
Conclusion
Hashes and IoCs
Initial Look
This is apparently a Darktrack 5.0 builder “with all plugs”. We’ll see about that, I guess. As I researched this, it looks like Darktrack 5 (also called Darktrack Colorful) hasn’t been released yet.
Running the builder gives you a pop up / license agreement window, and also drops two files into the %TEMP% folder:
2lWVy5LvsEb3quWh6S.exe
MBvI0Nh1JQcmVthRdCAy6TfJ2FA.exe
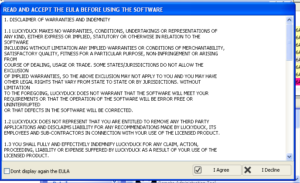
MBvI0Nh1JQcmVthRdCAy6TfJ2FA.exe is the panel executable that is presenting me with the EULA. Reading through the EULA doesn’t provide much interesting info. Someone (or some group) called Luckyduck appears to be responsible for Darktrack. One thing that’s interesting to me is that the English in the EULA starts out good, then gets noticeably worse as it goes along. Perhaps the beginning was just copied and pasted from somewhere else. The following snippet suggests that the product’s name is actually Darktrack Alien and the purported developer is this Luckyduck:
3. PRIVATE VERSIONS AND SOURCE CODE
3.1 THERE IS NO PRIVATE OR CUSTOM VERSION OF DARKTRACK ALIEN, IF YOU BOUGHT ANY KIND OF
DARKTRACK ALIEN VERSION THEN YOU BEEN SCAMMED.3.2 THE SOURCE CODE ARE FULLY CLOSE, ONLY THE CODER OF DARKTRACK ALIEN (LUCKYDUCK)
GOT
THEM, DONT TRY TO FIND THEM NEITHER YOU WILL NEVER FIND THEM SO DONT LOOSE YOUR TIME.
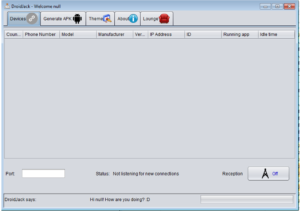
The panel is pretty nice looking, actually:
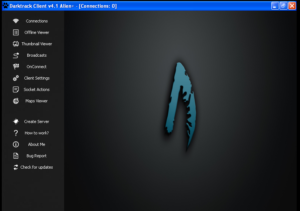
There’s a help section, which tries to connect to the “Darktrack Tube” found at https://www.youtube[.]com/embed/0hByqnu6-Z4. This’ll be good to dig through later. There’s also a nice “About Me” section:
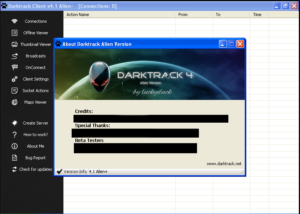
There are a bunch of names to look into someday, plus also what appears to be the website for Darktrack at www.darktrack[.]net. I also see that this appears to be Darktrack Alien 4.1, not the 5.0 version as promised by the original poster. Bug reporting is handled at https://forum.darktrack[.]net/.
Besides this stuff, the rest is sort of typical RAT panel features — client management panel, client builder/client settings, IP address map / victim geography, etc. The only problem is that one of the most important parts doesn’t appear to work — the client builder. If you can’t build your own clients, you can’t really do anything useful with this thing. It looks like this package came with a pre-built client from whoever cracked this (called “stub.exe”) but this won’t help anyone trying to create their own clients. Going back to the forum where I found this malware, the majority of ratings the post got indicated that the malware wasn’t functioning. I’m guessing that the only people who rated it as working were the original poster and his pals (or multis). I’m going to try to work with the stub.exe file anyway and see if I can get some more info about Darktrack from it.
Static and Dynamic Analysis
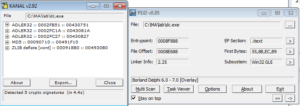
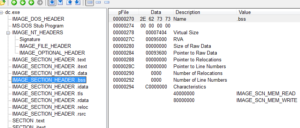
Taking a look at the stub.exe program, it’s a fairly big file (around 650k). It looks like it’s Delphi (ewww). Some people I know definitely are not fans of looking at entropy, but I like looking at it and it helps me, so bear with me if you disagree. Here’s an entropy plot of the stub.exe program before execution:
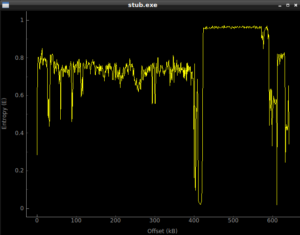
Looking at this, it seems fairly normal until you get to around 425k into the file, and then it looks like we have something there. Running the program, and then dumping the process with Volatility gives us something different, with the following entropy plot:
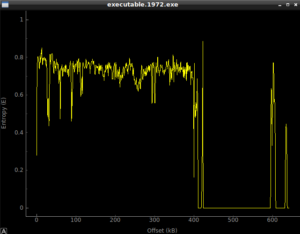
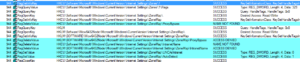
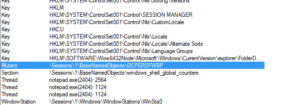
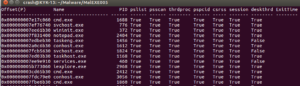
Whatever there was at the 425k area, it’s in use now. Looking in memory of the running stub.exe program, there’s some interesting stuff already:
xaf5c78 (40): C:\DOCUME~1\Owner\LOCALS~1\Temp\Klog.dat
0xaf5cf8 (40): C:\DOCUME~1\Owner\LOCALS~1\Temp\Klog.dat
0xafcfa8 (47):
[String Search]-(9/27/2017 / 8:13:43 PM)
4
0xafcfe8 (46):
[String earch]-(9/27/2017 / 8:13:43 PM)
0xafd028 (46):
[String Search]-(9/27/2017 / 8:13:43 PM)
0xb042d8 (91): Num 4AltAltAltAltfNum 2Num 2Num 2Num 4ShiftShiftShiftShiftShiftShiftShiftShiftShiftShift4
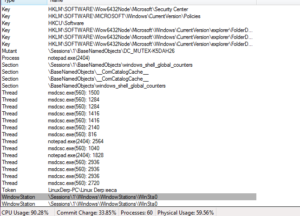
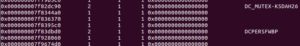
Further on, we see what could be the config info of the client:
080IAM010010DAR8K89TR3SDTACK
4.1 Alien+
Local User
123456
127.0.0.1
notepad.exe
SYSTEMROOT
WINDIR
APPDATA
The item at the top is the mutex used by this malware, I presume (to be confirmed) to ensure that only a single instance is running at a time on the victim’s machine. You can also see the default password and host (123456 and 127.0.0.1) listed there as well. We’ll have to see what the rest is for. Perhaps notepad.exe is injected or something.
Looking through the rest of the stuff revealed in memory suggests the following capabilities for Darktrack, though this needs to be confirmed by deeper digging:
- Keylogging (keylogger file will be stored in the victim’s %TEMP% folder in a plaintext file called KLog.dat)
- Possible Anti-Sandbox / Anti-VM capabilities (against Virtual Box and Sandboxie)
- Anti-Debugging (reference to KERNEL32.IsDebuggerPresent and even a reference to SoftIce?)
- Credential stealing:
- Outlook/Exchange
- Firefox
- Skype
- YandexBrowser
- Comodo Dragon
- Chrome
- Possibly some Anti-AV capability
- Possible harassment feature (open and close optical drive)
- Supports Windows versions from Windows 2000 through Windows Server 2016 Technical Preview
There was another interesting string found in memory:
C:\Users\gurkanarkas\Desktop\Dtback\AlienEdition\Server\SuperObject.pas
This might provide another username to follow up on.
Disassembly
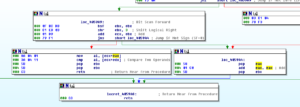
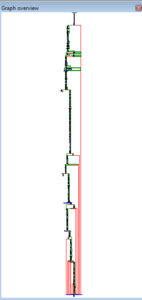
Let’s start looking at this thing in the disassembler. Opening this in Ida 5.0 (as I am still waiting for all that money from the Nigerian Oil Minister to hit my account, I cannot yet afford a paid copy of Ida) reveals some further detail behind some of the information we found by looking at it statically and dynamically. My earlier pieces on this site included many, many screenshots from Ida (and often from Olly) but I’m not going to kill you with 47 pictures of disassembly. However, I’ll try to mention a few things I found while poking around in the guts of the unpacked stub.exe.
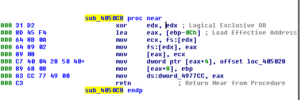
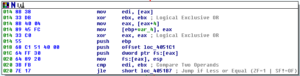
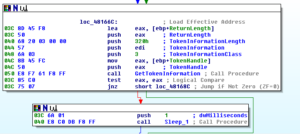
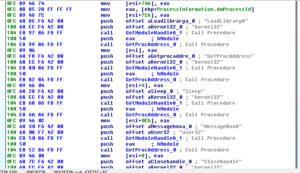
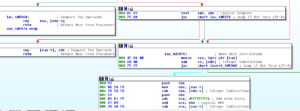
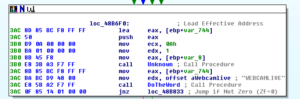
Subroutine 425654 appears to be where libraries and functions are loaded. Take a look at the following:
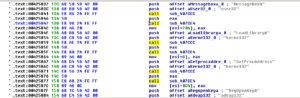
KERNEL32.LoadLibrary and KERNEL32.GetProcAddress are basically ubiquitous. LoadLibrary takes a single parameter (the name of the library) and GetProcAddress takes two parameters, the handle to the module (library) and the name of the process to load. The sequence of events looks like this to me (at this time):
- Push a proc name, then a library name. The stack should look like this, from last to first: library name, proc name
- Call LoadLibrary (the return should be the handle to the library, which should go into EAX). At this point, the stack should just have the proc name on it.
- PUSH EAX to put the handle to the library on the stack, so now we should have: Handle to library, proc name
- Call GetProcAddress which should then return the address of the export
- Then we see that the address of that proc is being moved into a structure, e.g.: MOV [ESI+20H], EAX, that is, the returned handle of the proc is being moved into the memory address of wherever ESI+20H is in that instance of the program
- Iterates for many libraries and procs
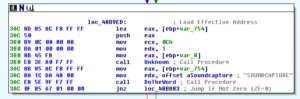
I’m going to call sub 407CCC “MaybeLoadLibrary” and sub 407CE4 “MaybeGetProcAddress” [note that 407CCC was later revealed to be a call to KERNEL32.GetModuleHandle]. I’m also going to create a structure in Ida and then start labelling all of these references to proc addresses so it’s easier to read than [ESI+0CH].
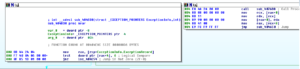
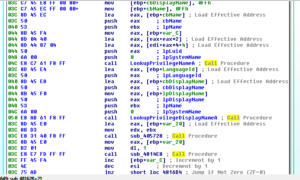
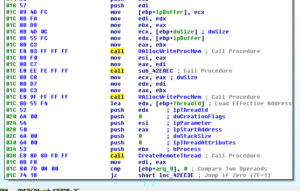
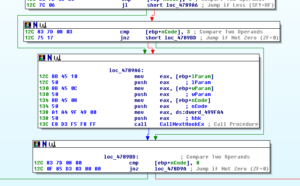
449E60 looks like the sub that actually does the stored login harvesting from the various browsers supported by this RAT. Sub 460740 is a giant control subroutine containing a very large and ugly switch statement with 154 cases:
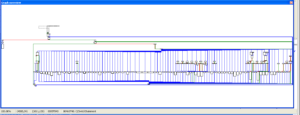
Within this switch statement, there are several cases that will pass the locations of stored credentials for the supported browsers and then call sub 449E60 to acquire them. The cases are:
0x54h Yandex Browser
0x55h Comodo Dragon
0x88h Google Chrome
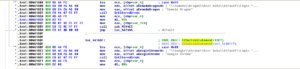
The following parts of the switch statement refer to targeting other platforms, though with different underlying mechanisms than the areas above:
0x60h Skype
0x89h Firefox
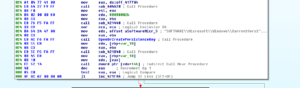
An additional interesting case in this switch statement is 0x72h, System inventory (gathers some info about processor architecture). Stub.exe determines whether or not the processor is 32- or 64-bit using code beginning at location 4605C3. The subroutine called in that area, 45E340, makes a call to KERNEL32.IsWow64Process and determines the architecture based on the returned value.
I also found an evasion subroutine at 425F34. This sub starts by going to the `Software\Microsoft\Windows\CurrentVersion` Registry key. It checks the Product ID for the string `76487-337-8429955-22614` which would detect Anubis Sandbox. Other evasion subroutines I found are as follows, with their associated product:
- Sub 425E7C checks Product ID for string `76487-644-3177037-23510` for CWSandbox
- Sub 425DC4 checks Product ID for string `55274-640-2673064-23950` for Joe’s Sandbox
- Sub 425DA0 calls KERNEL32.GetModuleHandle to check for `dbghelp.dll` for Threat Expert
- Sub 425D7C calls KERNEL32.GetModuleHandle to check for `SbieDll.dll` for SandBoxie
- Sub 425B78 VMXh magic value trick to detect VMWare
- Sub 425C20 checks for `VBoxService.exe` as a running process to detect VirtualBox
- Sub 4260C4 checks for debuggers via a call to KERNEL32.IsDebuggerPresent
- Sub 42611C checks for debuggers by determining if the debug flag is set to 1 in the PEB at offset 0x2h
- Sub 4261E8 checks for software breakpoints (0xCC, Int 3)
- Sub 426174 not 100% sure — checks for `DAEMON` and also does the PEB antidebugger check again
- Sub 42624C checks for Syser Debugger via a call to KERNEL32.CreateFileA to check for the files `Syser`, `SyserDbgMsg` and `SyserBoot`
- Sub 4262AC checks for SoftICE Debugger via a call to KERNEL32.CreateFileA to check for the file `SICE`
- Sub 4262E8 checks for SoftICE Debugger via a call to KERNEL32.CreateFileA to check for the file `NTICE`
- Sub 426158 is the master anti-debugging sub for two user mode methods above, which calls 4260C4 and 42611C
- Sub 4265AC is the master evasion sub, as it contains calls to the evasion subs listed above
One strange thing about this sample is that despite all of these evasion methods above, some of the functionality of the malware still appears to execute even though I’m not running it in a hardened VM. I’d expect none of the functionality to work given that this malware is detecting my VM.
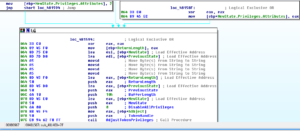
Subroutine 45F938 looks like the overall system inventory sub. I was able to identify the following subroutines within it, and their apparent functions:
- Sub 45F4A4 Identify the Windows Version
- Sub 45F0F4 Identify user type (administrator / regular user)
- Sub 405344 Appears to be called to store system inventory information once gathered
- Sub 45F8C0 Has calls to USER32.GetForegroundWindow and USER32.GetWindowText the result of which is stored
- Sub 45D74C is used to identify the presence of services on the victim machine by the port that is in use. The specific services that the malware looks for are: FTP (ports 20/21), SSH (22), Telnet (23), SMTP (25), Whois (43), DNS (53), DHCP (68), HTTP (80/8080), POP3 (110), NetBIOS (137/138/139), IMAP (143/220), SNMP (161), IRC (194 [usually this is 6667? Looks like they are just using the “standard” ports]), SSL (443), SMB (445), Lotus Notes (1352), MS SQL Server (1433), Oracle (1521), NFS (2049), MySQL (3306), ICQ (4000), and VNC (5800/5900). Any other open ports are listed as “Unknow [sic] Service Port.”
Sub 45DED4 uses subroutine 45D74C above to identify open and closed ports and services
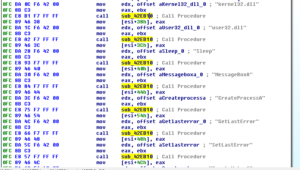
Sub 4423BC contains many function calls related to setting up for and taking what is probably a screenshot of the victim’s desktop. Sub 442020 looks like it could be the network communications startup subroutine. Besides seeing that there appears to be a user-agent construction section within this subroutine, there are also a bunch of unlabeled calls in there. Two of these look very much like they could be a call to WS2_32.WSAStartup and WS2_32.Socket based on the parameters being passed. I can’t discern any of the other function calls one would normally look for (things like listen, send, recv, getaddrinfo, etc.) based on the rest of the disassembly but I’m going to label 442020 as possibly the network communications startup subroutine. Sub 43BD50 appears to be a performance monitoring subroutine, based on information from a very old article located at (http://bcbjournal.org/articles/vol3/9906/Writing_a_Performance_Monitor.htm?PHPSESSID=058081f577534833ddc780e5995cdbae).
Going back to the C2 switch statement referred to earlier, located at 460740, there is what I refer to as a harassment section (sometimes referred to as “fun stuff” by the malware developers). This subroutine falls under case 0x61 in the main C2 subroutine and is also a switch statement with 15 cases. The cases and associated functionality are as follows:
0x1 Unknown
0x2 Disable shortcuts and the desktop
0x3 Enable shortcuts and the desktop
0x4 Hide Program Manager
0x5 Show Program Manager
0x6 Turn the monitor off
0x7 Turn the monitor on
0x8 Unknown
0x9 Force Shutdown/Poweroff
0xA Force Logoff
0xB Force Reboot
0xC Hide Taskbar
0xD Show Taskbar
0xE Open Optical Drive
0xF Close Optical Drive
45C218 is a network sniffing subroutine. The full functionality is not 100% clear, however the code will call WS2_32.WSAStartup, WS2_32.Socket and WS2_32.Bind before likely making a call to WS2_32.WSAIoctl and one other function. This appears to be designed to sniff all packets that the victim machine is exposed to.
At location 468894, one can actually see the PE header for an executable file packed with UPX. Sub 4484C0 references this location, and while it’s a bit difficult to see what’s going on due to indirect calls, it looks like this sub sets aside 175,616 bytes in memory and then unpacks the file into that. One of the parent subroutines of this one appears to actually be the code found at this Github page: https://github.com/jasonpenny/democode/blob/master/dGinaTest/BTMemoryModule.pas. It seems that the malware uses this to load and parse a PE header from a file (probably the UPX-packed file we are discussing) and then appears to use the code to then load a bunch of SQL Lite functions. I’m guessing that this file that is packed is probably SQL Lite and it is probably being used to store data about the victim’s machine, but I’m going to dump this file and take a look at it to be sure. Sub 4484E8 is the overall subroutine that is responsible for this, and I’m going to tentatively going to call this the “Unpack SQL Lite and Setup” sub.
45A360 appears to be the subroutine handling opening a chat window with the victim. Sub 45A4EC is strange. I believe this is some sort of encryption subroutine. It has a few dozen cross-references in the disassembly, and uses a strange 51-character string which is “Yhuol08uJhGfCVzzXdFG.==+t&t&y7877wSWqwDw12123ghhGTG”. I’m going to label sub 45A4EC as “MaybeEncryption” and keep moving on, and maybe I’ll see something that will shed more light on this if I run this in the debugger.
After pulling the UPX file out of the stub with Hiew, I unpacked it and it appears to just be a regular sqlite3.dll. The file did get a few detections on VirusTotal, but the detections aren’t really ones I would trust. Based my own examination of the actual contents this appears to just be a SQL Lite .dll. I noticed that the Darktrack builder appears to store victim information in a SQL Lite file, so maybe the developer just uses SQL Lite for storing the various information about victims both on the panel machine and on each victim machine.
Debugging
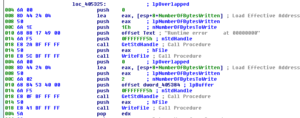
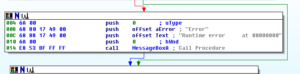
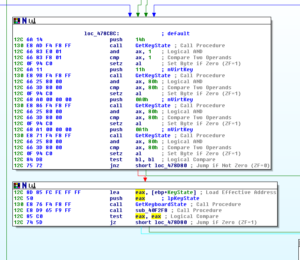
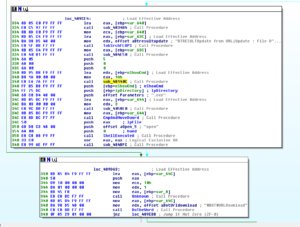
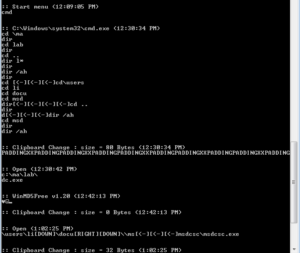
Running the stub.exe program through the debugger really helped to clarify some things that were not clear in the disassembly either because my older version of Ida didn’t work 100% correctly or because there were some indirect calls in the code that were hard for me to discern via the disassembly alone. What I’m calling the master evasion sub, 4265AC, actually has some other things going on in it that I didn’t see before. The first thing is that I see near the beginning of this sub that the program tries to load a resource called “settings” which I presume is the RAT config info. Stub.exe isn’t able to load this from the .rsrc section. The error returned is “ERROR_RESOURCE_NAME_NOT_FOUND”. I’m not sure what’s wrong, but I’m going to keep going and see what other stuff I can find out via the debugger.
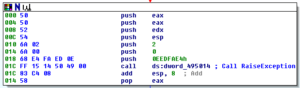
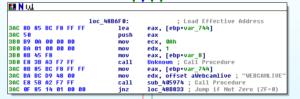
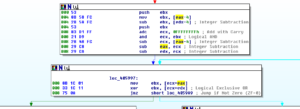
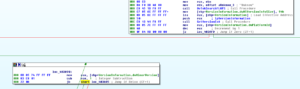
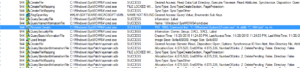
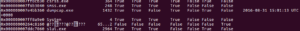
A small detail that I assumed was the case was confirmed while I was running stub.exe in the debugger. The RAT client does use the mutex to ensure that only a single instance of the malware is running on a victim’s machine at a time. Sub 42651C controls this. It will make a call to another subroutine to create the mutex and then it will make a call to KERNEL32.GetLastError. It will compare the error returned with the constant 0xB7 (which would indicate “ERROR_ALREADY_EXISTS”). If it does already exist, then the malware will terminate, while success or any other error returned will allow the malware to continue to execute. See below from my debugger:
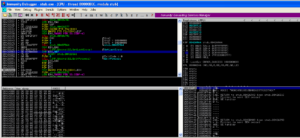
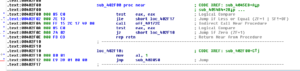
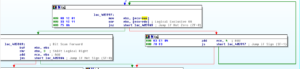
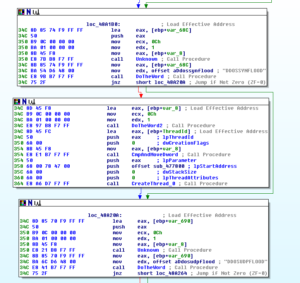
Sub 426CF0 is another subroutine that has been greatly filled in via the debugger. This subroutine handles several calls to various WS2_32 functions that handle connection to the RAT host. Moving back over to the evasion subroutine beginning at 4265AC, I set a new entry point to put us back in the various anti-analysis tests. Sub 425FEC appears to get the current user name and compare it with the string “CurrentUser”. I’m not sure what this is supposed to accomplish. In doing some reading on the subject, this appears to be another way to detect certain sandbox environments. Another thing that became clear in the debugger is that the main evasion sub contains two calls to KERNEL32.GetTickCount to add this timing check to the other anti-analysis techniques. The two KERNEL32.GetTickCount calls are located at 426710 and 426858, and in this case the malware will terminate if there has been more than five seconds between the two calls.
Sub 425040 is very interesting now that I’ve been able to look at it in the debugger. I had previously named this as some sort of function loading subroutine, but running it in the debugger I see that there are some more interesting things going on. The Darktrack stub will invoke a new notepad.exe process and then allocates memory and starts to write to those newly allocated areas with what appear to be procedures to load from KERNEL32. It then tries to start a remote thread in that notepad.exe process, which in my test environment crashes notepad. After this, stub.exe goes a bit bonkers and enters a very processor intensive infinite loop (perhaps this is some sort of evasion technique itself). I’m going to step back a bit and see if I can get into other functions.
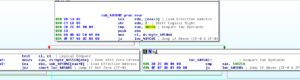
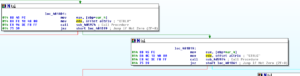
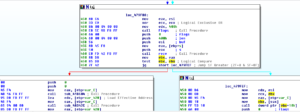
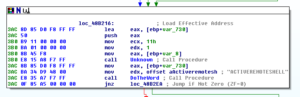
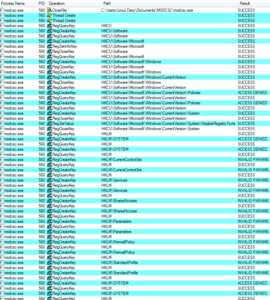
One subroutine that I am very interested in is sub 45A4EC. This one contains a really nasty looking string as mentioned earlier (“Yhuol08uJhGfCVzzXdFG.==+t&t&y7877wSWqwDw12123ghhGTG”). Earlier I’d guessed that this is some sort of encryption subroutine, so I set a breakpoint on this subroutine to see what happens here. When the breakpoint hit, I saw something very interesting which looks a lot like RAT C2 communication being used here:
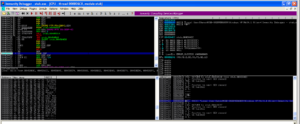
We can see a lots of things passed here, such as the logged in user, the Windows version, the Darktrack version, the active window, the user type (administrator or regular user), and the password for this Darktrack stub (in this case, the default “123456”). After observing this subroutine for a bit, I noticed that there is a loop starting at location 4552AF and looping back from 455329 that uses that big ugly string to do a some sort of multibyte XOR of the system inventory information that we saw being passed to this overall subroutine before:
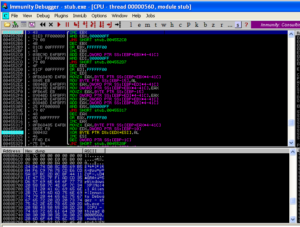
I tried to arrange the screen to best view the encryption/decryption loop and the area of memory where it can be seen that the string is in fact being encyphered via XOR. While it appears to be some sort of multibyte XOR, it’s not actually as simple as just taking the key and the plaintext and doing a multibyte XOR. There is some mechanism that I can’t discern that is adding some extra complexity to how this encyphering is being handled. Maybe someone with more experience with this could look at this someday. In the meantime, I suppose it would be possible to take the code from the malware, put it into some format of your choice, and use that to decypher traffic. I actually tried this just to be sure — I took the final encyphered text, put it where the plaintext should go, and watched as I ran the malware again and it decyphered what it had previously encyphered with this subroutine.
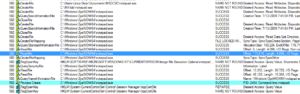
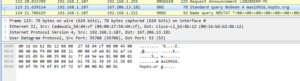
I tried manipulating various things in sub 426CF0 which appears to be the subroutine to connect to the RAT host. Looking in here confirms that the port used by this stub is 9633 by observing the call to WS2_32.htons. After stepping through this subroutine and trying to keep things going in the right direction by modifying memory or the code, I was able to get the stub to connect to my panel:
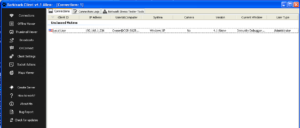
Right clicking on the connected Darktrack client reveals some options. Control center is probably the most interesting, but it can still be seen that from this quick menu there are options to obtain information about the victim’s machine, execute commands or open web pages on the victim’s machine, uninstall the RAT client or options to help organize the victim in the overall list of infected machines.
The control center is pretty slick and has several screens worth of options:
The interface is actually very nice, I’m impressed by how this was put together, compared with some other malware samples I’ve worked with. Looking through all of these options, this confirms a lot of functionality that was either suspected based on the static/dynamic analysis or was seen in the disassembly and debugging:
- File manager functionality
- Registry editing
- Process manager
- Windows Services manager
- Installed application enumeration
- Active connections enumeration
- Startup manager
- Clipboard manager
- Surveillance functionality (online and offline keylogger, remote desktop connection, remote camera and microphone capture, remote shell, saved passwords harvesting, ability to download/upload and execute files on the victim’s machine)
- Hosts file editing
- Script execution
- Dialog box generator
- Networking management features (share enumerator, LAN scanning, port scanning, TCP sniffing)
- Information gathering (system privileges and monitoring)
- Miscellaneous features I classify as harassment features (ability to send a key input to the victim’s machine, print a file, text to speech, user chat, restart/lock/logoff/shutdown the machine)
- Skype management (obtain users, contacts, file transfers, and conversation info)
- RAT client management features (restart, close, uninstall, share client)
As I said before, some of these are very nice. For instance, the process manager functionality is very well presented and allows the RAT controller a lot of control over the running processes on the victim’s machine (such as suspending the process, killing it, altering the priority, etc.). The remote shell functionality is very easy to use, also.
This pretty much wraps up everything I’m interested in looking at in this particular malware sample.
Conclusion
Darktrack RAT has a nice user interface and contains a lot of functionality that would be of interest to a malicious actor. Nothing is too notable (when compared with other RATs) however the interface for the RAT controller is well-designed and easy to use. Some flaws emerged from examining this sample. For instance, the evasion subroutines do not fully work, even in an obvious analysis environment. The evasion routines also appear to be old/outdated due to some of the platforms targeted. Obfuscation of traffic via the XOR-based scheme is weak, especially when the key is so easy to obtain from the stub file and in the worst case one can just use the malware’s own subroutine to encypher or decypher traffic. The lack of a working client builder is a major issue, but this might have been an issue introduced by whoever cracked this particular copy of Darktrack. Overall, this was an interesting malware sample to analyse and reverse (even if it is Delphi).
Hashes and IoCs
Builder Archive
MD5 367ba50a6f212e9f722b72a92ae9b7a8
SHA-1 bf6f497f654c920d6485d723d310a7373f2b72f1
File Type RAR
SSDeep 393216:gO3Otn+wKEqgvtYgeUNDA1H0Kw1VvUACZ1t6HoF:MxK8CTXTw1VvSZ1tR
File Size 18.01 MB
Builder Main Executable
MD5 c2cae2249e422ec8d3d2da5712679262
SHA-1 35e2c4d521d0ce60ae1a78f88f116057367d83fa
Imphash 029f303dc25c06dd65b86262c6a9ed20
File Type Win32 EXE
SSDeep 98304:Bkl5IlOxWJBWN6O5zjfxIhItSQfmK36t+iuHWWoS9sHOAaMnq6+q3SATTzGypMLD:eKupzlefQOKU+iuHkORMnq6+4eLoMSQL
File Size 6.5 MB
Stub.exe
MD5 edc9c0a3eaaf592dba89ec3735ef022b
SHA-1 4c1196733e6bafa0b7d3e078896d0937111a9440
Imphash ee46edf42cfbc2785a30bfb17f6da9c2
File Type Win32 EXE
SSDeep 12288:BOqvQomCg4G6q90tmPvj+GU/ttJuqwh3EQiXRUVZs4ixsiNhkApRaw:9oovgbAKvBgtJuqwh3EQihUb1ifNh
File Size 627.5 KB
Dumped Stub.exe
MD5 ecae681b11dac1bb8facde439229f50a
SHA-1 391a75dc8b37a8716cb5856fae7c0dd965162930
Imphash 62201a8d9ef3cb9372a8618dffb33bd0
File Type Win32 EXE
SSDeep 12288:dOqvQomCg4G6q90tmPvj+GU/ttJuqwh3EQiXRUqr:5oovgbAKvBgtJuqwh3EQihUq
File Size 627.5 KB
UPX Packed sqlite3.dll
MD5 63f87edc6c0fcc88c9951119e39ccd7f
SHA-1 7e19bea3abcfec0ef66d3ee0ae01ce8812f6e32a
Imphash 9b821a35d20f9a8955f8d5e54b175675
File Type Win32 DLL
SSDeep 3072:XsABLvEx/5jcESAxpeGwuYwTPk9cJx9RjhkZ726EJS2vICXPnwL1nPTsb+jRsR8:XZLvExxjcixs+XNhkA6GSaRXfy1nbO
File Size 215.36 KB
Unpacked sqlite3.dll
MD5 dddf597f6546ddae942ce08bc773f646
SHA-1 6dde01d2699afa2c731a7344f5e8ad129a98ce4a
Imphash af2a1cf0ae9d12b4ef9c165cff60e4b3
File Type Win32 DLL
SSDeep 6144:OICvMnOTvcfgA0qBlJ89Ojo33C1oVDtY4sG2/WctyzuYf0ob8L23/8O:uvMnAA9BleOjoH4Ktm+jbFX3/l
File Size 379.86 KB
Stub.exe
MD5 edc9c0a3eaaf592dba89ec3735ef022b
SHA-1 4c1196733e6bafa0b7d3e078896d0937111a9440
Imphash ee46edf42cfbc2785a30bfb17f6da9c2
File Type Win32 EXE
SSDeep 12288:BOqvQomCg4G6q90tmPvj+GU/ttJuqwh3EQiXRUVZs4ixsiNhkApRaw:9oovgbAKvBgtJuqwh3EQihUb1ifNh
File Size 627.5 KB
Stub-specific signatures:
Mutex: 080IAM010010DAR8K89TR3SDTACK (hard-coded to this stub, but likely changeable in a working builder)
C:\DOCUME~1\Owner\LOCALS~1\Temp\Klog.dat (keylogging results in plain text)
Ports 4157 and 9633 are two default ports in this particular copy of the Darktrack builder
XOR key: Yhuol08uJhGfCVzzXdFG.==+t&t&y7877wSWqwDw12123ghhGTG
Example C2 communication:
Local User|Owner@[redacted]|Windows XP|No[refers to web camera]|4.1 Alien+|Immunity Debugger – stub.exe – [CPU – main thread, module stub]|ENU|Administrator|123456|C:\DOCUME~1\Owner\LOCALS~1\Temp\|1|