Continuing on the subject of honeypots, I wanted to see if I could get something set up as an ICS/SCADA honeypot. I’ve noticed traffic on some of the GRAB series honeypots that could be Modbus connections, for instance. I’m also pretty interested in ICS/SCADA in general, so I looked into whatever I could find regarding honeypots that I might be able to set up myself. In the end I set up a single Conpot honeypot, and I thought I’d share my notes in case it helped save someone some time.
I identified several potential honeypots to try:
– Digital Bond’s SCADA Honeynet
– Cisco CIAG’s SCADA Honeynet
– Fieldbus Honeypot
– SHaPe honeypot
– Conpot
Ultimately, Conpot was the only one I got to work. Here are my notes on everything:
Digital Bond’s SCADA Honeynet
This sounded like it would be the most robust and realistic of all the honeypots that I could find, but I ran into issues during installation. First, the documentation and system is from 2006, so a lot of the instructions are really out of date (for instance, one document referred to installation on an Ubuntu 6.x system). I ran into a few issues while installing dependencies, but I was able to get past those — specifically, instead of xlibs-dev, install libx11-dev, and automake1.11 instead of automake1.9. The real issues came when I tried to install VMware server. This used to be freely available, but isn’t really available anymore from VMware (I’ll explain what I mean by this). The installation instructions from Digital Bond specifies a link to download an old version of VMware server for Linux (1.0.2) and this link still works, however with my current version of Ubuntu (16.04) I ran into too many issues with the installation and just gave up on it.
Cisco CIAG’s SCADA Honeypot
This system requires Scientific Linux 3 and a formatted, empty floppy disk. Next…
Fieldbus Honeynet
This system came up during searches for these types of honeypots. The info sheet indicates that it handles Modbus and also lists some contact info for creators, however trying to reach out to them resulted in bounced email. Not sure if this is publicly available, and searching didn’t turn up any other email addresses to use to contact them. The overall project page can be found here.
SHaPe Honeypot
I found this one through an interesting academic paper about electric power substation honeypots. They have the source up here. I liked the idea that this would be a module for Dionaea, which meant that I could either add this module to an existing honeypot, or quickly set up a new honeypot running Dionaea (which is very easy) and just use it to run this module. I ultimately ran into various issues during setup, and at this point I was pretty burned out and not interested in pursuing this anymore. If you have more luck, please let me know and maybe I’ll give it another try if you can send me some ideas on what to try.
Conpot
This was the first such honeypot I had heard of, and ended up being the one I installed. They have a great website for the honeypot, and installation was pretty easy. Instructions were sparse but clear. I installed from the git repository, not using pip. I did have issues during installation, but nothing out of the ordinary. One issue was that I needed to install libmysqlclient-dev (apt-get install libmysqlclient-dev), no big deal. The other issue I had, though, appears to be a known issue but again the fix was pretty simple. Basically, I had to downgrade stix and cybox to lower versions and then I was fine:
sudo pip install 'stix>=1.1.1.5,<1.2.0.1'sudo pip install "cybox==2.1.0.12"I copied both of those right out of the issue logged on the github page and then I was no longer getting errors. To keep Conpot running in the background after logging out, I used setsid in case you’re wondering how to do that. Finally, to test the honeypot, I went ahead and tried connecting to it:
2016-08-03 15:42:07,581 New Modbus connection from x.x.x.x:38816. (x-x-x-x-x) 2016-08-03 15:54:31,643 New Modbus connection from x.x.x.x:38828. (x-x-x-x-x)
Seems to be working (the xs are in place of my connection info).
I found a great article by Darren Martyn over at xrl about OPSEC for honeypots. There’s a lot of great points there, but overall — DON’T leave the default Conpot settings in place when you run your honeypot. Go to the /conpot/templates/default directory (or the directory for whatever template you are using) and look in the .xml file for that template. Here is my default Conpot template before editing:
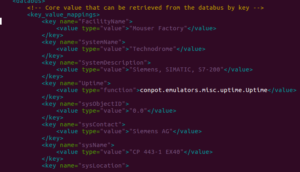
You should see the issues right away. Darren’s post highlights some of these, but to recreate his quick check on this, I did a search on shodan.io and look what I found:
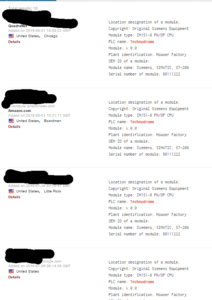
Don’t be these people. Change your default settings. I found dozens of these honeypots all over the world this way. One note — you might go to change the template settings in the /opt/conpot/templates directory. Per this post, go to /usr/local/lib/python2.7/dist-packages/Conpot-0.5.1-py2.7.egg/conpot/templates [you may have a different version number than I do] and change your templates there. You can test it quickly to be sure by just pulling up your site in your web browser.
Digital Ocean is not great as a host for this type of honeypot because it’ll show up as such in a search — putting it another way, why would an ICS/SCADA system be on a Digital Ocean VPS, or AWS, or GoDaddy.com? Doesn’t really make sense, but for now that’s what I have so I went with another droplet there. Ideally I’d put this new honeypot somewhere that it might actually make sense to have such a system, but I don’t have access to any such facility. I did, however, look around the area and do a little research on some ICS/SCADA sites, and entered values that should be plausible enough to collect some attacks in the honeypot. I’m not going to post any of that info here as that would potentially ruin the honeypot I set up, but what I’d say is look around the area where your honeypot is hosted and try to create a plausible “identity” for your system. Try to also pick a system that 1) uses Modbus and 2) might actually be in use at your choice of cover story. We’ll see how successful I was at setting this up, and hopefully at some point soon I’ll have some interesting info to share about this new system.
I’ve decided to place ICS/SCADA honeypots under the series JUMPSEAT.