Honeypot update – I still have four Dionaea honeypots running in NYC, Frankfurt, Bangalore and Singapore (the GRAB series) and a single Conpot running in NYC (JUMPSEAT).
I didn’t have a similar issue in September as I did in August (when the sheer volume of traffic caused the honeypots to run out of inodes in the first 3-10 days of the month) though Frankfurt ran out towards the very end of the night on the 30th of September, so that cut it close a bit.
GRAB-NYC03:
Connections: 752,296
Unique IPs: 19,507
Files Downloaded: 5
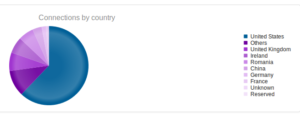
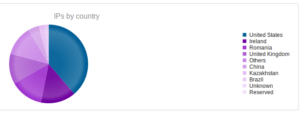
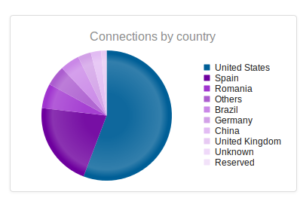
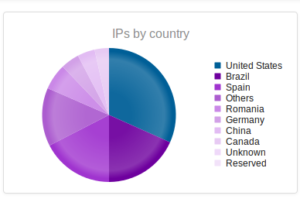
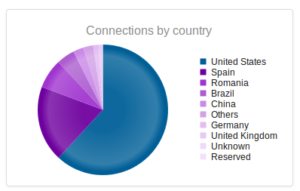
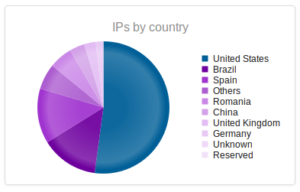
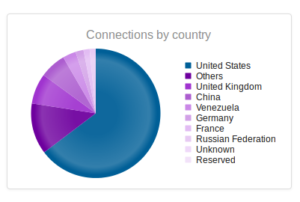
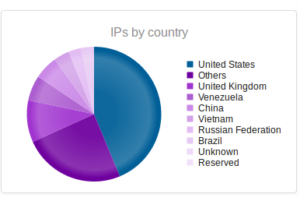
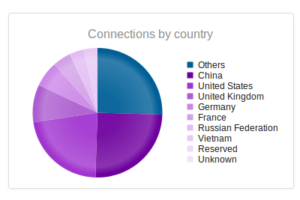
Interesting to see Kazakhstan make the list this time, with Romania making up a sizable portion of the totals this time around.

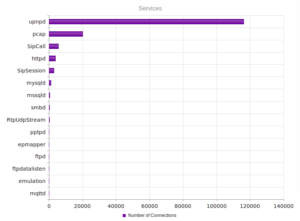
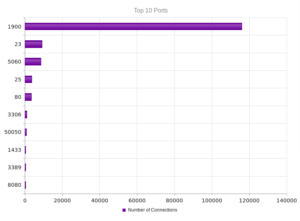
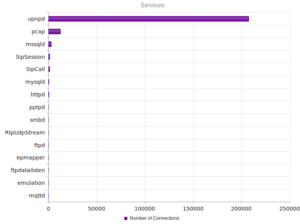
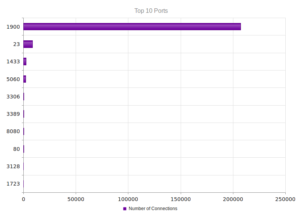
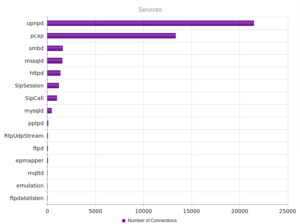
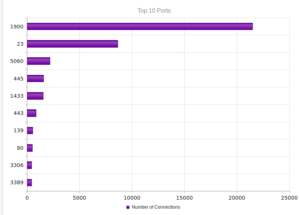
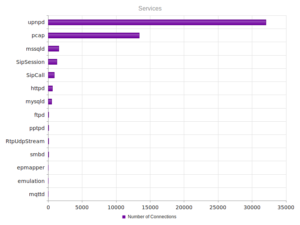
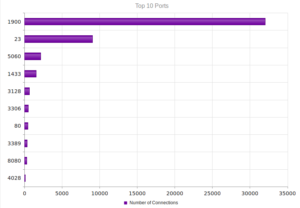
UPnP, again, strongly the most popular, and therefore no surprise when we look at the ports:

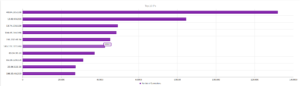
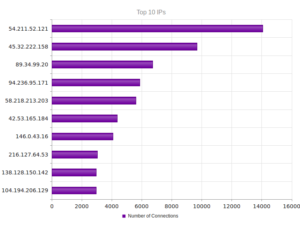
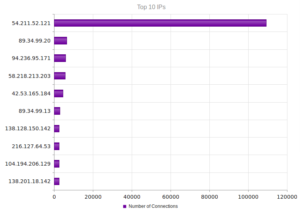
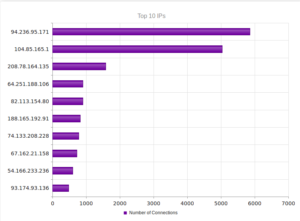
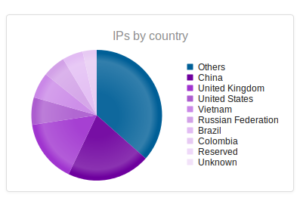
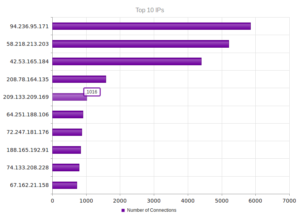
The top IP address, 40.84.185.138 leads back to Microsoft, actually, as do the next three addresses. 191.237.45.46 apparently leads back to Microsoft also, but this particular entry gets associated with someone apparently with Microsoft in Brazil (Benjamin Orndorff, who apparently is located in Seattle). Maybe this is just a provocation… The next two after that lead back to hosting providers in Europe, while the one after that, 65.19.129.154, seem to lead back to an electric company in California, with a NOC in Sterling, VA. The last two are Microsoft and a hosting provider in Canada.
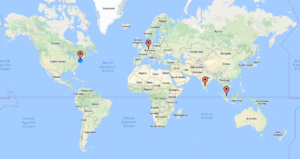
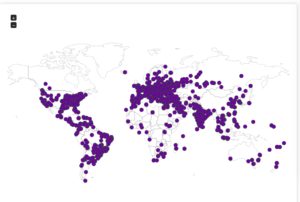
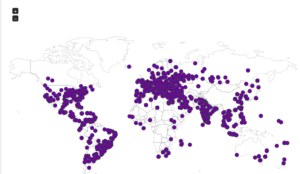
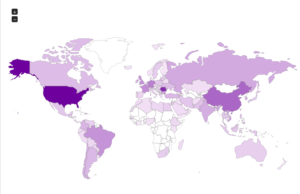
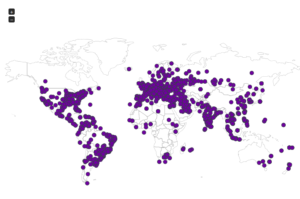
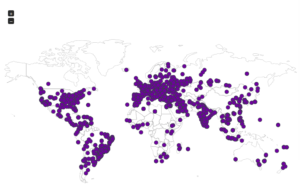
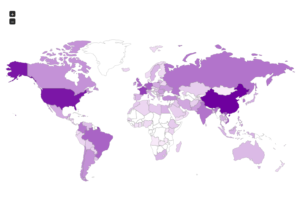
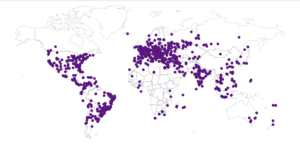
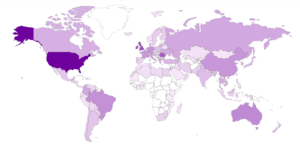
Here’s a map showing the attacker locations:
Next is the Frankfurt honeypot:
GRAB-FRA01:
Connections: 1,127,930
Unique IPs: 20,659
Files Downloaded: 15
Pretty spectacular number of connections – this is a new personal record for any of my honeypots.


Vietnam making the top 3 this time!
Similar results in terms of the shape of the graph for services, but wow – over a million UPnP connections.

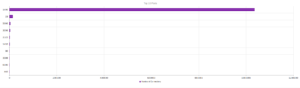

The top IP address leads back to some person in Vietnam. The second highest leads back to that electric company. Turns out it’s actually a hosting provider (Hurricane Electric), so not mysterious anymore. The remainder are hosting providers in France, Hong Kong, and also some of the same parties from Microsoft that we saw earlier with GRAB-NYC.
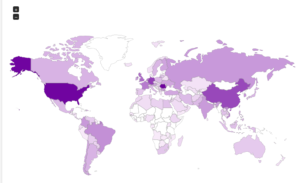
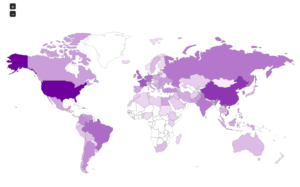
Now for the maps:
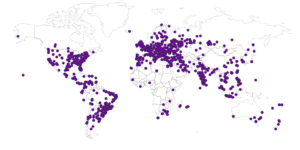
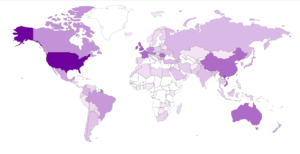
GRAB-SIN01:
Connections: 500,737
Unique IPs: 21,688
Files Downloaded: 10,518
Again, not a mistake – this honeypot set a new record for number of samples collected. Like last month – almost ALL of these downloads were Conficker variants. I did find one other piece of malware in there (Parite-C). I find it really interesting that there is so much Conficker in this region, and how it doesn’t seem to spread to my other honeypots.


India makes the list, which is a first, as well as Venezuela and Ireland.


Services and ports are pretty much in line with other regions.

Microsoft coming in at number 1! And 2, and 3, and 4, 5… and 7… and 10. What the hell? The rest were just some hosting providers in various places (one in India).
Now, maps:
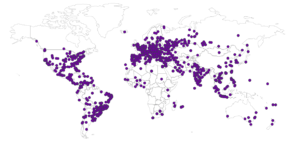
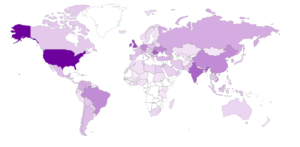
Bangalore:
GRAB-BAN01:
Connections: 457,464
Unique IPs: 21,221
Files Downloaded: 2
As usual, dismal number of files collected from Bangalore. Also, like last month,this honeypot has the highest number of unique IPs of all the GRAB honeypots.


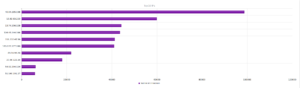
Services/ports in line with other regions:


Microsoft dominates these results also, 7/10. The rest are hosting providers (including one from AWS).
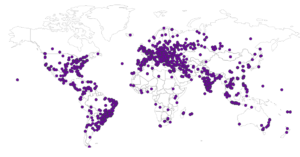
Some maps:
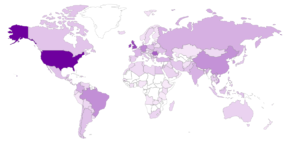
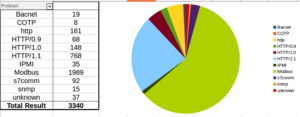
Much more activity on JUMPSEAT in September, here are the total connections by protocol:
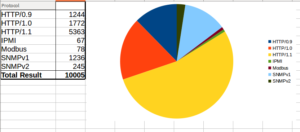
Last month saw Modbus as the most popular protocol, followed by all variants of HTTP, so much different this month. Perhaps the parties involved noticed that my honeypot doesn’t quite seem right and stopped bothering.
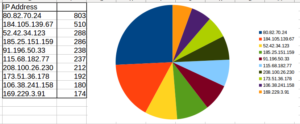
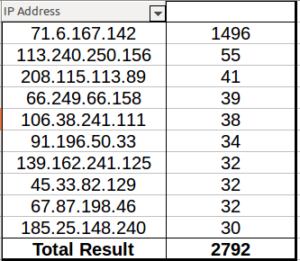
Lots of activity, but nothing as clearly anomalous as when we had shodan.io scanning the honeypot in August. 80.82.70.24 leads back to a hosting provider in Seychelles. 184.105.139.67 is Shadow Server, again. 52.42.34.123 leads back to Amazon while the next two lead back to Poland. One of them is actually a security company I’m familiar with! Hello there! The last one leads back to UC Berkeley.
That’s it for September, on to other things.